New update of RustBucket Malware introduced several changes. Now the malware is more securely fixed in the systems of its victims and evades detection by security software. Though the most concerning feature there is its enhanced ability to attack macOS. What is RustBucket malware? Researchers from Jamf Threat Lab discovered RustBucket in the spring of… Continue reading RustBucket Malware Attacks MacOS More Effectively
Tag: macOS
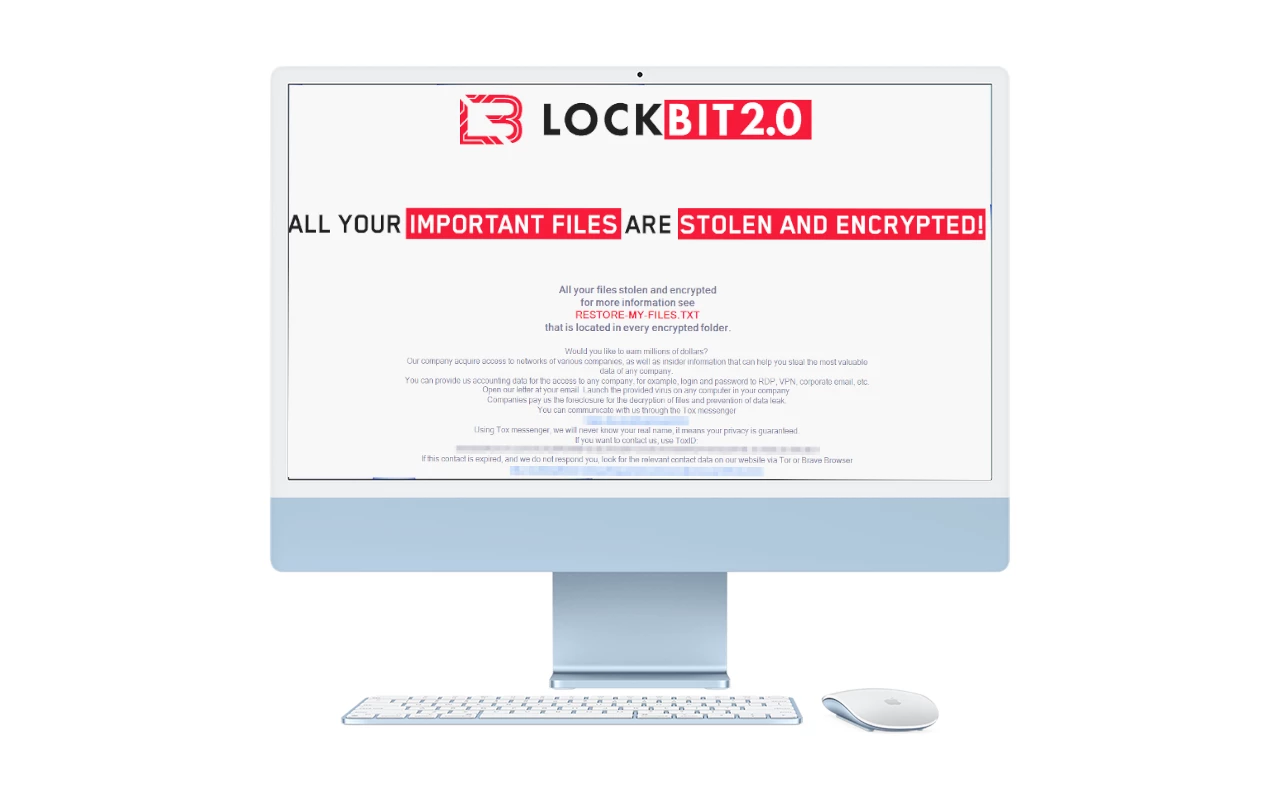
LockBit Releases World’s First macOS Ransomware
LockBit, an infamous ransomware gang that became a major threat actor over the last two years, released the variant of its ransomware for macOS. Previously, this system was considered safe from ransomware, as no known samples were targeting it specifically. Currently, LockBit’s product is considered the first ransomware that breaks that rule. What is the… Continue reading LockBit Releases World’s First macOS Ransomware
Lazarus Hackers Attack MacOS Users by impersonating Crypto[.]com
Sentinel One has discovered that the North Korean hacker group Lazarus is targeting macOS users selectively. Attackers are using fake Crypto[.]com jobs to hack developers and digital artists in the cryptocurrency community. It is assumed that in the long term, attackers aim to steal the digital assets and cryptocurrencies of their victims. By the way,… Continue reading Lazarus Hackers Attack MacOS Users by impersonating Crypto[.]com
CloudMensis Malware Attacks MacOS Users
ESET experts have discovered the CloudMensis malware, which is used to create backdoors on devices running macOS and subsequently steal information. The malware received its name due to the fact that it uses pCloud, Dropbox and Yandex.Disk cloud storages as control servers. Let me remind you that we also wrote that Vulnerability in macOS Leads… Continue reading CloudMensis Malware Attacks MacOS Users
Privacy Access Tokens to Replace CAPTCHA Real Soon
CAPTCHA, a well-known test for website visitors to prove they are humans, not robots, rapidly grows obsolete. There are ways to break or bypass CAPTCHA, and there are obvious inconveniences these tests bring to clients when deployed on websites. Luckily, the progress won’t cease, and the replacement is coming. We’re talking about Privacy Pass –… Continue reading Privacy Access Tokens to Replace CAPTCHA Real Soon
Apple paid $100,000 for macOS camera and microphone hack
Information security researcher Ryan Pickren told how he received a large reward from Apple for hacking the camera and microphone in macOS. He also discovered vulnerabilities in Safari and macOS that could be used to hack into a user’s online accounts. Back in 2020, Ryan Pickren received a $75,000 bug bounty from Apple because he… Continue reading Apple paid $100,000 for macOS camera and microphone hack
Critical vulnerability in Office fixed, but macOS update is delayed
As part of the January Patch Tuesday, Microsoft engineers fixed a critical vulnerability in Office that could allow attackers to remotely run malicious code on vulnerable systems. The RCE vulnerability identified as CVE-2022-21840 can be exploited on target devices with even the lowest privileges and in simple attacks that require user interaction. Basically, the user… Continue reading Critical vulnerability in Office fixed, but macOS update is delayed
Vulnerability in macOS Leads to Data Leakage
Microsoft said that attackers could use a macOS vulnerability to bypass Transparency, Consent, and Control (TCC) technology and gain access to protected user data. Back in the summer of 2021, a research group informed Apple developers about a vulnerability dubbed powerdir (CVE-2021-30970). The bug is related to the TCC technology, which is designed to block… Continue reading Vulnerability in macOS Leads to Data Leakage
Attackers again deceived Apple’s notarization process
In September 2020, I talked about how the Shlayer malware successfully passed the notarization process and was able to run on any Mac running macOS Catalina and newer. Now there is information that the attackers again deceived the notarization process. Apple introduced the “notarization process” security mechanism in February of this year: any Mac software… Continue reading Attackers again deceived Apple’s notarization process
Shlayer malware bypassed Apple security checks
Security expert Peter Dantini discovered that the Shlayer malware bypassed Apple’s checks: it successfully passed the software notarization process and could run on any Mac running macOS Catalina and newer. In February of this year, Apple introduced a new security mechanism: any Mac software distributed outside the App Store must go through a notarization process… Continue reading Shlayer malware bypassed Apple security checks