Scientists from the Swiss Higher Technical School of Zurich have developed an attack that allows not to enter a PIN code when making contactless payments with Visa Credit, Visa Electron and VPay cards. This attack allows an attacker who owns the details of a stolen contactless Visa card to use the card to pay for high-value goods, whose price is much higher than the limit of contactless transactions. And an attacker doesn’t need a PIN.
A report describing this attack technique has already been published in the public domain, and experts intend to arrange a full presentation of their research at the IEEE symposium, which will be held in May 2021.
“The attack they invented is very difficult to detect because the attacker would be like a regular customer who pays for a purchase using a smartphone. In reality, the attacker will pay with a stolen contactless Visa card, which is hidden somewhere on his body”, – say the scientists.
This attack does not require sophisticated equipment, only two Android smartphones, a special app created by the research team, and the contactless card itself. At the same time, the application installed on both smartphones will work as an emulator of a PoS terminal and an emulator of the card itself.
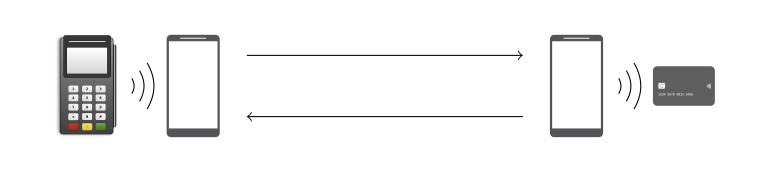
As a result, the attack looks like this: a smartphone that imitates a PoS device is placed next to a stolen card, and a smartphone that acts as a card emulator is used to pay for goods. The idea is that the PoS emulator asks the card to make a payment and modifies the transaction details, and then transmits the changed data via Wi-Fi to the second smartphone, which ultimately makes a large payment without having to enter a PIN code (after all, the attacker changed the transaction data in this way to not require PIN entry). A demonstration of the attack can be seen below.
Our application does not require rooting or any clever Android hacks. We have successfully tested it on regular Pixel and Huawei devices”, — write the researchers.
If we talk about the technical side of the issue, such an attack is possible due to the design flaws of the EMV standard and the Visa contactless protocol. These bugs allow an attacker to modify the contactless transaction data, including those fields that are responsible for transaction details and the need to verify the cardholder.
Essentially, the attacker informs the terminal that PIN verification is not required, and that the cardholder has already been verified on a consumer device (for example, a smartphone). Moreover, these modifications are carried out on the smartphone where the PoS emulator is running and are performed before being sent to the second smartphone. That is, already changed information is transmitted to the real PoS device, and it cannot determine whether the details of the transaction have been modified.
To find these problems, the researchers used a modified version of a tool called Tamarin, which was previously used to detect complex vulnerabilities in the TLS 1.3 cryptographic protocol (PDF), as well as in the 5G authentication mechanism (PDF).
Using the same tool, experts identified another potential problem that affects not only Visa but also Mastercard. The researchers did not conduct field tests of this bug for ethical reasons.
Here’s how the experts describe the second problem:
Also, our symbolic analysis revealed that during an offline contactless transaction using a Visa card or an old Mastercard, the card is not authenticated with the terminal through ApplicationCryptogram (AC) – a cryptographic proof of the transaction created by the card that the terminal cannot verify (only the card issuer can) … This allows attackers to trick the terminal into accepting an invalid offline transaction. Later, when the acquirer adds the transaction data to the clearing record, the issuing bank will find the wrong cryptogram, but by that time, the criminal has long disappeared along with the goods”.
Let me remind you that I also talked about the interesting SpiKey technique that allows opening the lock by recording a sound of a turning key. Moreover, soon will be produced a real hackers Tamagotchi. Do you already feel your own defenselessness in the new digital world?

