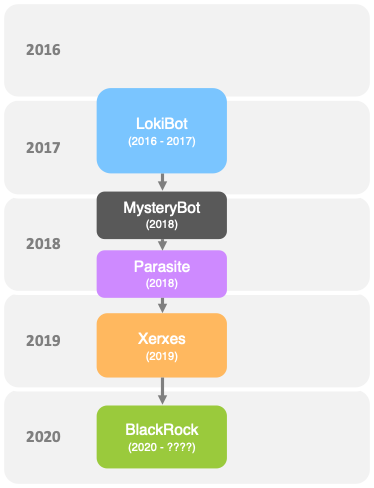
Researchers from ThreatFabric have published a report on the study of a new Trojan on Android OS, called BlackRock. This malware is aimed stealing data from various applications, including dating applications, instant messengers, bank products, social networks and so on. In total, the trojan can attack 337 applications.
This threat was first noticed in May of this year, but its BlackRock roots go much further. The fact is that the trojan is based on the “leaked” source codes of another malware, Xerxes, which, in turn, was also based on the sources of other malware.
It is noted to the BlackRock were added new features, in particular designed to steal user passwords and bank card information.
Overall, BlackRock works in the same way as most other Android bankers; it just targets more applications. So, the trojan steals user credentials, but if possible, prompts the victim to enter payment card information (if the target application supports financial transactions).
“Data collection and theft is done using overlays. That is, the malware detects when a user tries to interact with any legitimate application and displays its own fake on top of this window, where the victim enters his credentials or card details”, – written by ThreatFabric specialists.
To be able to display such windows on top of other applications, the trojan uses an old trick and asks the user for access to the Accessibility Service. Having received these rights, the malware gives itself other necessary permissions on its own, and then completely gets administrator access on the device by using Android DPC.
ThreatFabric researchers write that most BlackRock overlays are designed to attack financial applications as well as social media. However, there are overlays for other types of applications, including dating, news, shopping and so on. A full list of targeted applications can be found in the expert report.
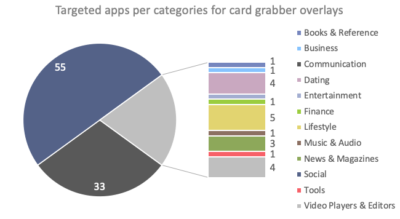
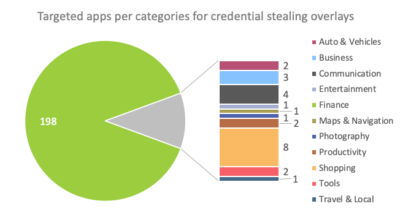
In addition to imposing phishing overlays, the Trojan can perform other malicious operations:
- intercept SMS messages;
- use SMS flood;
- spam all contacts with predefined SMS;
- run specific applications;
- intercept clicks (keylogger);
- show push notifications;
- sabotage the operation of anti-virus applications.
BlackRock is currently spreading through scam sites that disguise itself as fake Google update packages. Until the Trojan was found in the official Google Play Store.
Let me remind you that I recently wrote about two new malware, that can steal cookies from Android apps.

