GitHub developers have issued a warning about the appearance of the new Octopus Scanner malware, which is distributed ton the site through malicious Java projects.
Octopus Scanner was discovered in projects managed with the Apache NetBeans IDE, a tool used to write and compile Java applications.
After a tip received in March from information security researchers, the developers found 26 repositories containing malware. The list of repositories for the warning, unfortunately, is not attached.
“When users downloaded any of these 26 projects, the malware behaved like a self-propagating worm and continued to infect local computers. Octopus Scanner scanned the workstation for a local installation of the NetBeans IDE and implemented it in other victim Java projects”, – explain GitHub representatives.
Malware was adapted to work with Windows, macOS and Linux, and ultimately downloaded the Remote Access Trojan (RAT), allowing its operators to dig into files on the victim’s computer in search of confidential information.
GitHub reports that the Octopus Scanner campaign lasted several years. The oldest sample of malware was uploaded to VirusTotal in August 2018. Although only 26 repositories with traces of Octopus Scanner were found on GitHub, experts believe that over the past two years, much more projects have been infected.
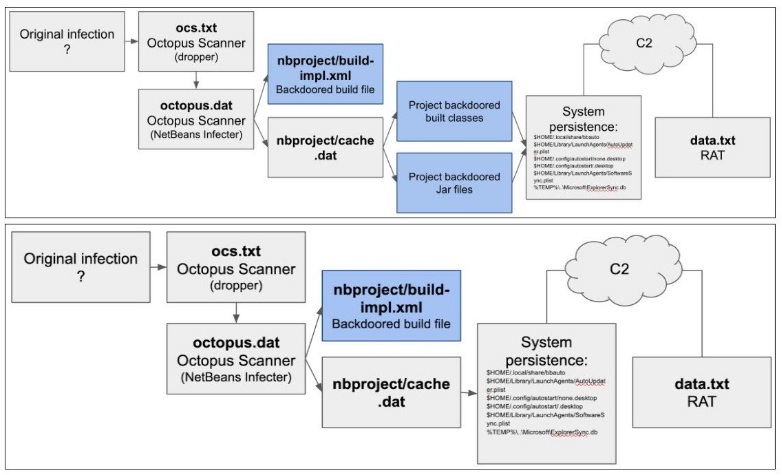
Apparently, the real purpose of these attacks was to place the RAT on the machines of people working on important projects or in large companies developing software. This allowed attackers to steal confidential information about upcoming releases, proprietary source code and even backdoors, embed in corporate or other closed-source software.
“Interestingly, this malicious program specifically attacked NetBeans, because today it is not the most common Java IDE. If the creators of the malware spent time implementing this malware specifically under NetBeans, this could mean that it was either a targeted attack, or they probably already had malware implementations for build systems such as Make, MsBuild, Gradle, and so on, and it could spread unnoticed”, — write GitHub experts.
Let me remind you that only recently GitHub representatives web service warned users of a massive phishing attack called Sawfish.

