Information security researchers at ReversingLabs reported the discovery of 725 malicious libraries that stole the contents of the clipboard in the official RubyGems repository.
RubyGems is a package manager for the Ruby programming language. According to their own site statistics, the repository contains around 158 thousand packages (called gems) with nearly 49 billion total downloads.
A complete list of libraries can be seen here.
Malicious packages were uploaded to RubyGems from February 16 to February 25, 2020 from two accounts: JimCarrey and PeterGibbons.
Researchers write that the malware was removed from RubyGems as early as February 27, two days after ReversingLabs notified developers of its finding.
All detected malware were clones of various legitimate libraries. They used the typosquatting technique, that means they had names deliberately similar to the originals, and even worked as intended, but also contained additional malicious files.
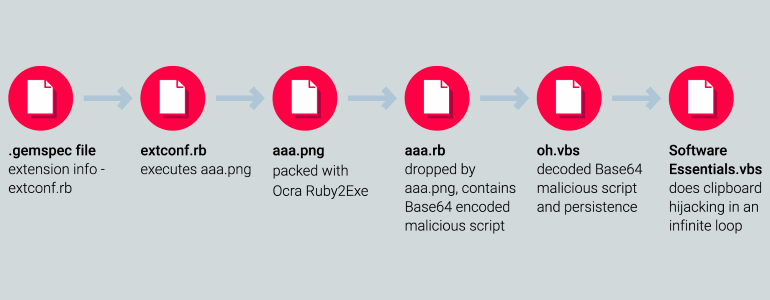
An additional file built into each such package was called aaa.png. Despite the extension, this file was not a PNG image. In fact, it was a Windows PE executable.
By the way, I have already written about how cybercriminals encrypt malware in images: for example, MyKingz botnet uses Taylor Swift photo to infect target machines.
Installing any of the malicious libraries caused a chain of the following actions:
- The PE file created a Ruby script called aaa.rb containing the Ruby interpreter and all the necessary dependencies to run;
- this script created a Visual Basic script called oh.vbs;
- the script created a key for autorun in the registry;
- the startup key executed the second Visual Basic script every time the computer started or rebooted;
- the second script intercepted the data sent to the clipboard, and looked for templates similar to the addresses of cryptocurrency wallets, and replaced them with an attacker’s wallet.
ReversingLabs writes that thousands of users later have downloaded these libraries. However, judging by the attacker’s Bitcoin address, during all the time of the campaign’s activity he was not able to intercept any payments, changing the address to his own.
Researchers believe that behind this attack is the same person or group that loaded malicious libraries into RubyGems earlier, in 2018 and 2019. Both incidents were distinguished by the use of similar methods, and the goal was stealing cryptocurrency from users.

