Avast analysts suddenly got the source codes for the GhostDNS exploit. The experts got access to the source thanks to an error from an unknown hacker.
GhostDNS is a set of exploits for routers that uses CSRF queries to change DNS settings and then redirect users to phishing pages (where from victims are stolen credentials from various sites and services).
Researchers say that an unknown hacker uploaded an unprotected password-protected KL DNS.rar archive into an unnamed file exchange website, containing a malware and several phishing pages. At the same time, the attackers seemed to forget that Avast antivirus was installed on his machine with the active Web Shield component that protects against malicious web content. As a result, the file with the malware was analyzed by the Avast solution, and the researchers got access to the source code.
“We downloaded the linked file and found the full source code for the GhostDNS exploit suite”, — say the experts.
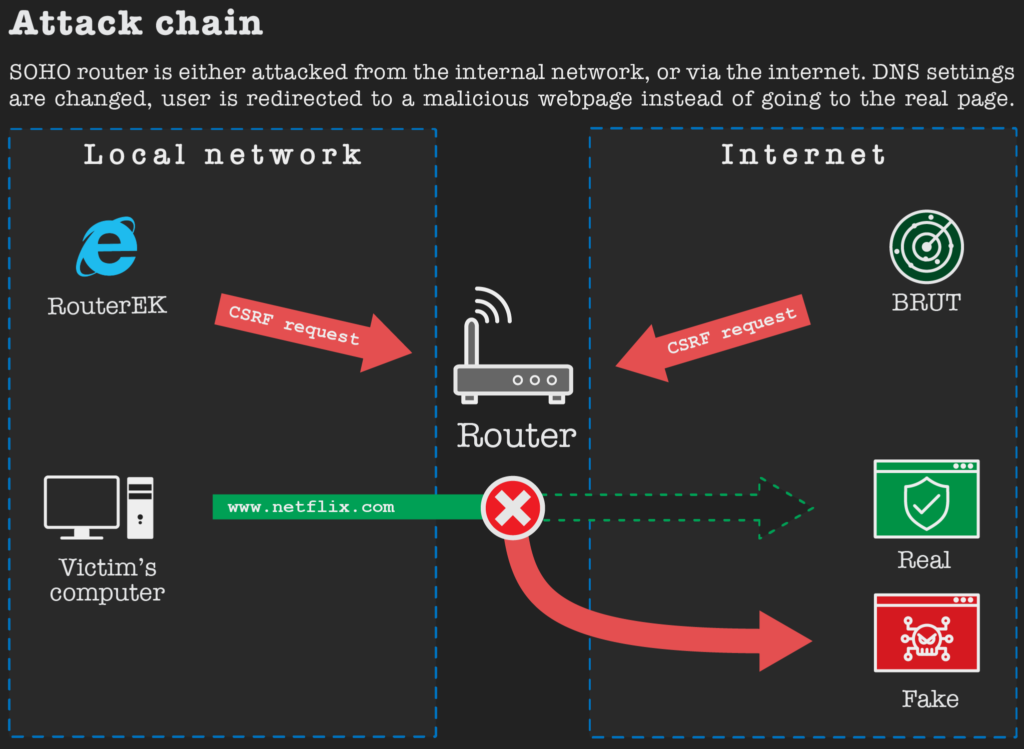
As showed analysis of the malware, the exploit kit used two methods to attack routers: Router EK and BRUT. Both methods used CSRF queries to change the DNS settings. So, Router EK is designed for attacks from the local network and requires the user to click on a malicious link. BRUT is a scanner that searches the Internet for insecure routers and attacks them (in this case, user interaction is not required).
Researchers found in the archive a list of prefixes for IP addresses in 69 countries of the world that the malware had to scan. For each prefix, were checked 65,536 addresses. Though majority of the target countries were in South America (Brazil was the most affected), victims are also found in the USA, Australia and Germany.
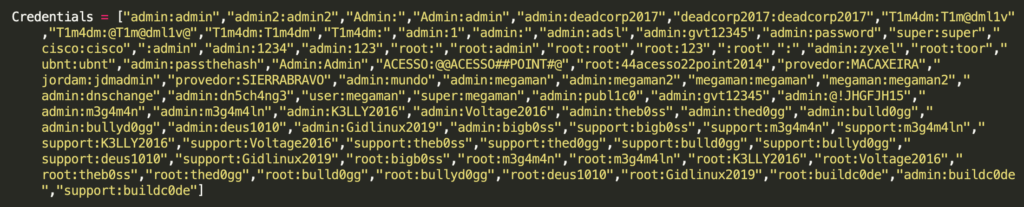
To gain access to the device and override the DNS settings, the new version of GhostDNS applied bruteforce, using a small dictionary containing a list of 22 default credentials. At the same time, older versions of the malware had a list of 84 credentials.
After gaining access to the device, the malware changed the DNS settings so they pointed to the attacker’s servers. To do this, a hacked version includes SimpleDNS Plus application.
In turn, RouterEK attacks victims through malicious advertising. If the user clicks on such a malicious ad, begins the search for the internal IP address of the router.
In this case, used a smaller set of credentials than in the case of BRUT. Avast analysts found a list of just eight usernames and passwords, all of which are most commonly found in Brazil.
If the credentials from the router successfully match, GhostDNS proceeds to the phase of displaying phishing pages. In the KL DNS.rar archive can be found several templates of such fakes that imitated the sites of the largest banks in Brazil and Netflix.
Let me remind you that recently I wrote that hackers spoof DNS settings to distribute fake coronavirus applications.

