Researchers from Carnegie Mellon University found that users seldom change passwords even after receiving data leakage messages. Scientists estimate that only a third of users actually update access to their sensitive data after being compromised.
Interestingly, this report, presented as part of the IEEE 2020 Workshop on Technology and Consumer Protection, is based not on survey data, but on actual browser traffic.
Experts examined the real traffic collected through the University Security Behavior Observatory, a research group, which users voluntarily enter and share the full browser history for academic research.
“The data for this analysis was collected from the home computers of 249 experiment participants for the period from January 2017 to December 2018. The information included not only web traffic, but also passwords stored in the browser”,- said the researchers.
As it turned out, of 249 users, only 63 had accounts on various hacked domains (those companies that publicly announced hacking and data leakage were taken into account).
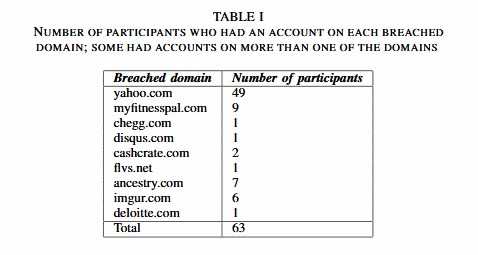
Of these 63 users, only 21 (33%) visited hacked sites to change the password, and of these 21 only 15 users changed their passwords within three months after the announcement of compromise.
In total, 23 passwords were changed on the above domains. So, among the experiment participants who changed their passwords, there were only 18 Yahoo! users; 31 more Yahoo! users (out of 49 in total) did not change their passwords, although everyone suffered from a data leak. 2 more users changed their passwords from Yahoo! twice, once after each report of compromise. 2 users changed their passwords on the hacked domain within one month after the hacking announcement, 5 people changed their passwords after two months and 8 people after three months.
Hence among other things, the researchers collected data on the passwords of the participants in the experiment, the team was able to analyze the complexity of their new passwords.
“Among the users who changed the passwords (21 people in total), only a third (9 people) changed them to more reliable ones. The remaining members of the control group came up with weaker passwords or passwords of a similar strength. As a rule, new passwords were created either by reusing sequences of characters from the previous password, or people simply changed the password to a different one, but already used for other accounts and also stored in the browser”, — said researchers from Carnegie Mellon University.
Experts say that hacked services themselves are responsible for issues with passwords, since they “almost never explain to people that they still need to reset similar and identical passwords for other accounts.”
By the way, turning to password managers is not an option – I recently wrote that experts have discovered vulnerabilities in popular password managers. And, by the way, it’s better not to check the password complexity on the Internet either, since, according to research, password meter services put Internet users at risk.

