Recently, I wrote all about the vulnerabilities of Intel and AMD processors, and in the meantime, a group of researchers from universities in the Netherlands and Switzerland published a report according to which modern RAM memory is vulnerable to Rowhammer attacks, despite all the protective measures taken by manufacturers over the past six years.
A new Rowhammer variation with TRR bypass is currently tracked under CVE-2020-10255.
Let me remind you that researchers from Carnegie Mellon University invented the original Rowhammer attack back in 2014. Its essence was that a certain effect on the memory cells can lead to the fact that electromagnetic radiation will affect neighboring cells, and the values of the bits in them will change.
“Over the years since then, researchers managed to prove that DDR3 and DDR4 memory could be vulnerable to Rowhammer, and they learned to exploit the attack through JavaScript and managed to adapt it against Microsoft Edge and Linux virtual machines. There’s even a Rowhammer variation that is dangerous for Android devices, and they’ve learned how to increase attack efficiency with video cards”, – write the researchers.
However, modern memory, in particular, uses Target Row Refresh (TRR) as a protection, and presents combination of various software and hardware fixes created over the past years. Mentioned above specialists managed to overcome TRR. They studied various TRR implementations from different manufacturers and developed a universal tool called TRRespass, which allows using the good old Rowhammer problem against modern and secure products.
“Thanks to TRRespass, even the latest-generation DDR4 with in-DRAM TRR on board, immune to all known Rowhammer attacks, are often still vulnerable to the new TRR versions of Rowhammer we developed”, — write the researchers.
In total, experts tested 43 DIMMs and found that 12 modules from three major DRAM manufacturers (Samsung, Hynix, and Micron) were vulnerable to new variations of Rowhammer attacks using TRRespass.
In addition, the researchers tested LPDDR4(X) chips, proving that they are also sensitive to the Rowhammer problem. According to tests, TRRespass helps to attack LPDDR4 used in smartphones Google, LG, OnePlus and Samsung.
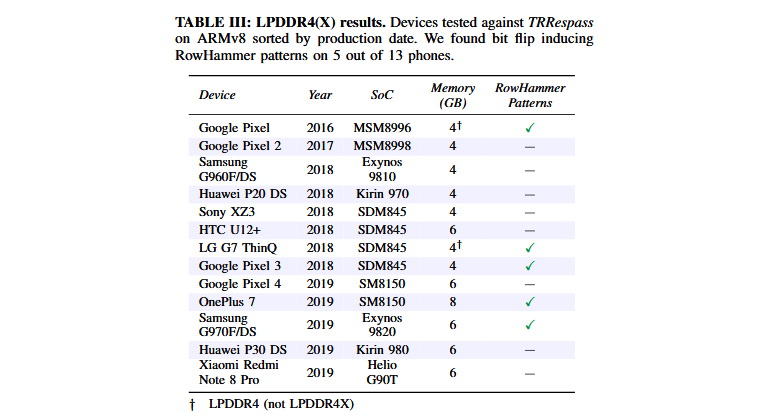
Researchers have already notified about the problems all manufacturers, whose products are affected by the new problem, but it is hardly worth waiting for updates soon.
“Unfortunately, due to the nature of these vulnerabilities, it will take a long time before will be taken effective measures to protect against them,” – note the authors of the report.

