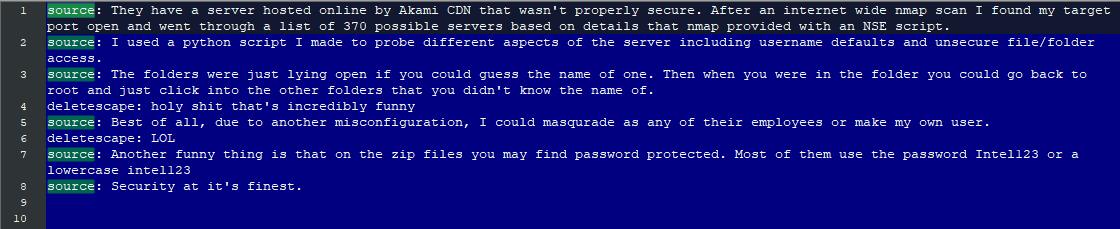
Swiss programmer Till Kottmann has been studying various dumps in the public domain for a long time and it looks like he found something interesting, so now the IT giant Intel is investigating the data leak.
Till Kottmann collects accidentally dumped data from large technological companies, information from which leaks through misconfigured repositories, cloud servers and online portals.
However, Kottman faced a different kind of leak this week.
An anonymous hacker, who claims to have hacked Intel earlier this year, uploaded Mega and sent Kottman a 20GB dump containing the company’s source code and internal documents (including those marked “confidential” or “secret, not for disclosure”). The attacker assured that this is only the first part of the stolen data. Currently, the dump can be easily found on torrent trackers, file sharing and so on.
“Interestingly, among the source codes, associated with Intel Purely Refresh for Xeon processors, were found comments, containing the word ‘backdoor’, and some encrypted archives from the dump were protected by simple passwords such as ‘Intel123’ and ‘Intel123′”, — says Till Kottmann.
Although I have talked about attacks on Intel processors before, but this is the first time I’ve heard about leaks in the company.
ZDNet journalists report that they showed the dump to experts, which specialize in Intel processors, and they considered the information reliable (although they wished to remain anonymous due to the ethical side of the issue).
According to the publication’s own analysis, the leak contains Intel’s intellectual property, including one that is related to the design and construction of various chipsets.
“The files contain technical specifications, product guides, and manuals for processors dated 2016”, – according ZDNet journalists.
Most of the documents and sources are related to the Kaby Lake platform and the upcoming Tiger Lake, although a small number of documents refer to other products, including those developed by Intel for SpaceX.
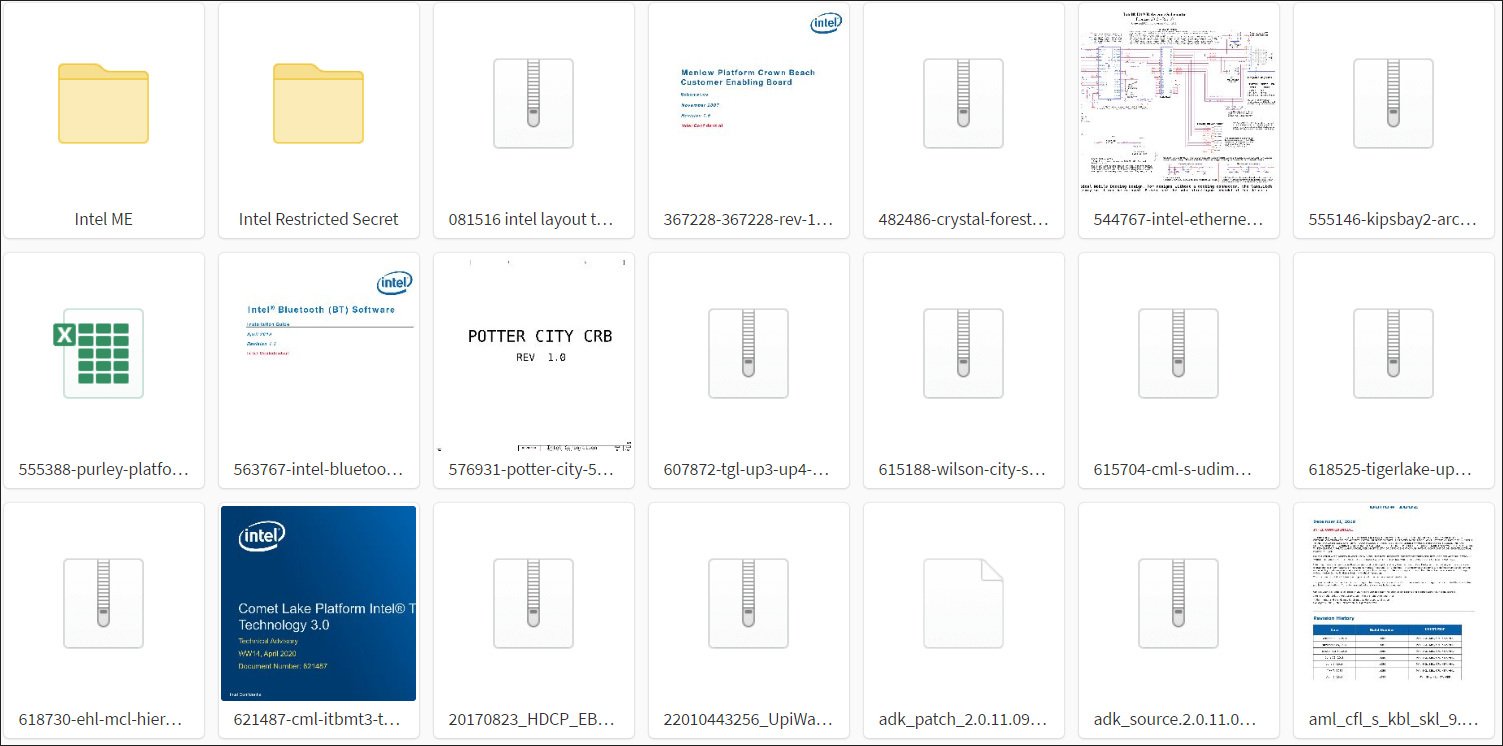
It seems that the dump does not contain confidential data about customers or Intel employees, but it is not known yet, to what other information the unknown hacker could have gained access.
Till Kottman writes that the dump includes:
- Intel ME Bringup guides + (flash) tools + samples for various platforms;
- Kabylake (Purley Platform) BIOS Reference Code and Sample Code + initialization code (some exported from git repos with full history);
- Intel CEFDK (Consumer Electronics Firmware Development Kit) sources
- Silicon / FSP source codes for various platforms;
- various tools for development and debugging;
- Simics Simulation for Rocket Lake S and possibly other platforms;
- various road maps and other documentation;
- Camera driver binaries developed by Intel for SpaceX;
- schematics, documents, tools + firmware for unreleased Tiger Lake platform;
- Kabylake FDK tutorial videos;
- Intel Trace Hub + decoder files for various Intel ME versions;
- Elkhart Lake Silicon Reference and Platform Code Samples
- Verilog related data for various Xeon platforms;
- debugging of BIOS / TXE builds for various platforms;
- Bootguard SDK (encrypted zip);
- Intel Snowridge / Snowfish Process Simulator ADK;
- various schemes;
- Intel Marketing Templates (InDesign).
Intel officials said they were already investigating the situation, but denied that the company was affected by the hack. Instead, they believe that the leak could have occurred because someone got access to the Intel Resource and Design Center, downloaded confidential data from there without permission, and then share it with a Swiss researcher.
Interestingly, the attacker himself claims that he gained access to the information through an unprotected server hosted in the Akamai CDN, and not using the Intel Resource and Design Center account.