Bitdefender experts have discovered a hacker group that is attacking companies around the world using a malicious plugin for 3Ds Max.
On August 10, 2020, 3Ds Max developer Autodesk posted a warning about the PhysXPluginMfx malicious module that abuses MAXScript, a scripting utility that comes with 3Ds Max.
“The PhysXPluginMfx plugin is capable of performing malicious operations through MAXScript, corrupting 3Ds Max settings, executing malicious code, and infecting other .max files on Windows and spreading them to other users who receive and open such files”, – warned Autodesk developers.
Bitdefender experts have studied this malicious plugin in details and now report that its real purpose was to deploy a backdoor Trojan that attackers used to search for confidential files on infected machines and then steal important documents. According to experts, the control servers of this hack group are located in South Korea.
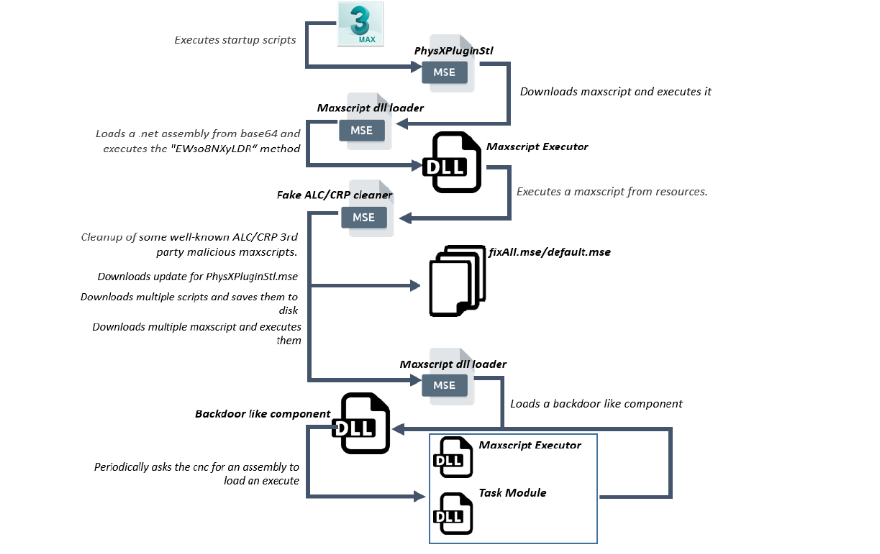
Researchers have found at least one victim of the attackers: it turned out to be an unnamed international company, which is currently conducting several architectural projects on four continents, together with developers of luxury real estate, totaling more than a billion US dollars.
“After examining our own telemetry, we found other [malware] samples that also interacted with this C&C server. This means that this group was not limited to developing malware only for the victim in respect of whom we conducted an investigation”, — write Bitdefender analysts.
These malware samples connected to the C&C server from countries such as South Korea, the United States, Japan, and South Africa. Based on this, the researchers suggest that there are other victims of the hack group in these countries. Although the malware has contacted C&C servers only within the last month, experts write that this does not mean that the group has been active for such a short time. Most likely, earlier the attackers simply used a different C&C server.
“They seem to have a good understanding of what they are doing and may have been unnoticed by security experts for a while”, — say the researchers.
Bitdefender analysts believe that this group can be an example of mercenary hackers that sell their services and engage in industrial espionage for other criminals.
Interestingly, this is not the first time that cybercriminals have exploited Autodesk products for their own needs. For example, in 2018, Forcepoint analysts published a report on an industrial espionage hack and attacking firm that using AutoCAD in their work.
In addition, this year cybersecurity experts discovered Valak malware, that steals corporate data using Microsoft Exchange servers.