BlackCat/ALPHV group recently announced on its victim shaming and extortion website that it had hacked into a luxury spa and resort in the Western United States. At one moment in the last 24 hours, ALPHV posted a website with the same victim name on the domain and their logo on the front page. The ALPHV website claims to care about people’s privacy, but allows anyone to view sensitive stolen data.
BlackCat/ALPHV published the leaked data
Cybercriminal groups that practice the double extortion have tried countless ways to shame their victims into paying. The latest innovation that increased the stakes comes from the ALPHV/BlackCat ransomware group. It commonly released any stolen victim data on the Darknet page. However, these days the group has begun posting the websites of individual victims on the public Internet, and the leaked data has been made available in an easy-to-search form.
This is a new but unsurprising evolution in extortion tactics. Alphv will likely use stolen email addresses to send a link to the site to impacted individuals. Other gangs have used similar strategies 2/3https://t.co/JE0V1wR2HY
— Brett Callow (@BrettCallow) June 14, 2022
The case with the luxury resort is among the first ones, but likely not the last. Hackers’ website claims to have the personal information of 1,500 resort employees and over 2,500 residents of the facility. At the top of the page there are two “Check Yourself” buttons, one for employees and one for guests. Brett Callow, a threat analyst at security firm Emsisoft, called the ALPHV’s actions a “cunning tactic” that is sure to worry their other victims.
Cybersecurity experts are surprised with what’s happening
Callow said most of the victim-shaming blogs maintained by major ransomware groups exist on obscure, slow-loading sites on the Dark Web. Users could reach those sites only with third-party software such as Tor. But the website created by the ALPHV as part of this new pressure tactic is available in the Surface Web. Hence, everyone who wants to check the information on the certain visitor is welcome. Companies are likely to be more concerned about the prospect of their data being shared this way than just being posted on an obscure Tor site whose URL almost no one knows,” Callow said. “It will piss people off and force them to react together.” Apparently, Callow alludes to the high probability of the FBI to pay attention to the gang with such sly tricks. And that is not the single case wherethe US law enforcement were going for these crooks.
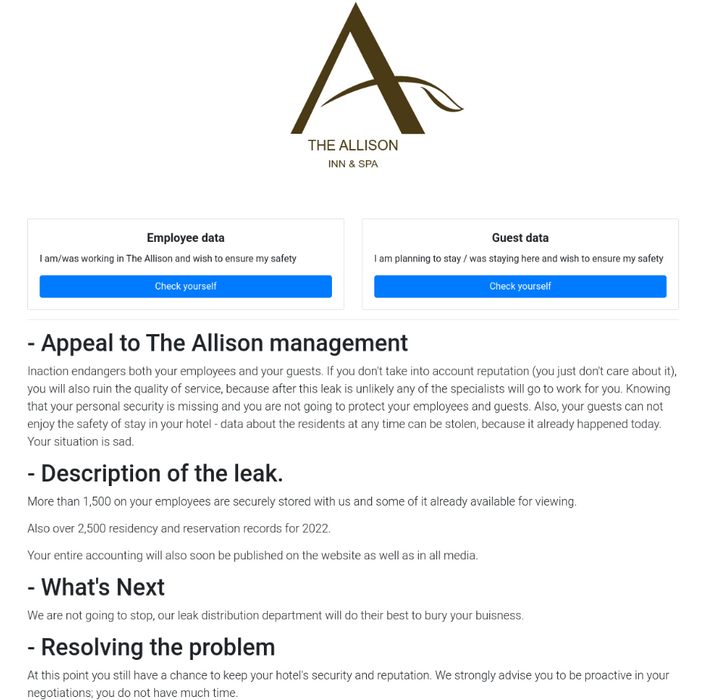
It’s unclear if the ALPHV plans to apply this approach to every victim, but other recent gang victims include a US school district and city. This is most likely a test run to see if it improves the results. “We are not going to stop, our leak distribution department will do everything possible to bury your business,” the victim’s website says. “At this point, you still have a chance to maintain the safety and reputation of your hotel. We strongly encourage you to be proactive in your negotiations; you don’t have much time.”
What is BlackCat/ALPHV ransomware?
Launched in November 2021, ALPHV is perhaps most notable for its programming language – Rust. Such a choice allows them to circumvent the detection from the conventional security solutions. Additionally, that made their malware cross-platform, so it can be freely launched on Windows and any of *NIX systems. ALPHV actively recruits operators from several ransomware organizations, including REvil, BlackMatter and DarkSide, offering partners up to 90% of any ransom paid by the victim organization.
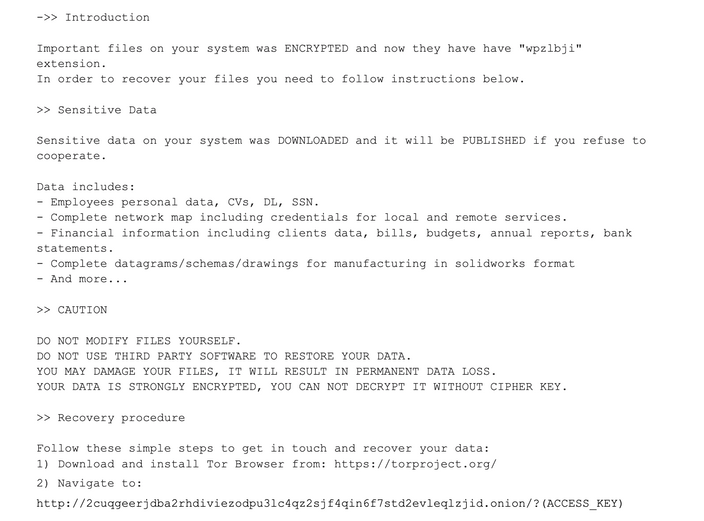
Many security experts believe that ALPHV/BlackCat is simply a rebranding of another ransomware group, Darkside, also known as BlackMatter. That gang is responsible for the 2021 Colonial Pipeline attack. This attack lead to fuel shortages and price spikes on the U.S. East Coast. That’s why, exactly, I have mentioned that the attention from law enforcement is not new for those people. Are they fearless now?
Let’s sum the things up
The fact that the ransomware group stepped up to posting the leaked info, and in particular the information about individuals, is outrageous. Even more disgusting is that they created a page for that in the surface web. Still, such a technique can turn positive for individuals whose data is leaked. Mr. Callow I have cited above supposed there may be a silver lining to this ALPHV innovation, mentioning his wife’s conversation with Cl0p ransomware gang representatives.
“On the positive side, tricks like this mean that people can find out that their personal data has been compromised. Cl0p sent a letter to my wife last year. The company that lost her data still hasn’t made the information public or notified the affected people (at least she hasn’t heard anything from the company).”
Sure, receiving the leak notification in such a manner is not a pleasant thing. But that is way better to remain unaware at all, like it happens pretty often. Who knows, maybe that case will push the stakes and force the companies to claim about the leaks as soon as they are uncovered? What a time to be alive.

