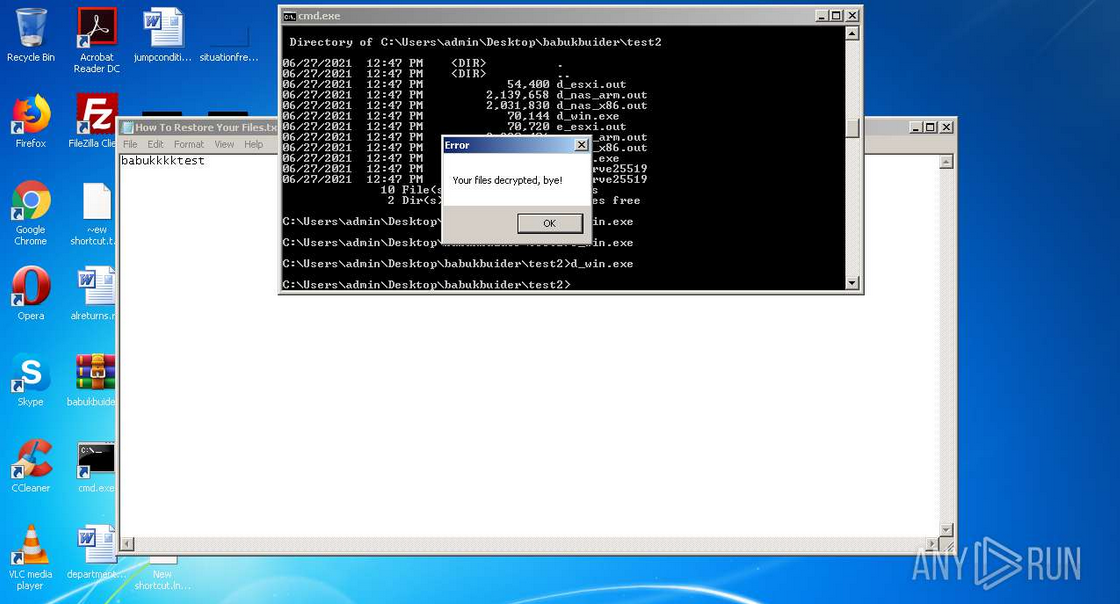
The Babuk Locker ransomware builder has appeared in the public domain. With its help anyone can design its own ransomware, the well-known information security expert Kevin Beaumont said on Twitter.
The malware is already uploaded to VirusTotal.
The Record, which has already studied this leak, reports that the Babuk Locker builder can be used to create custom versions of the ransomware and be used to encrypt files on Windows systems, ARM-based NAS, VMWare ESXi servers.
The constructor also creates its own decryptor for each ransomware that can be used to recover the encrypted files of each victim.
The leak came two months after Babuk Locker operators announced cessation of their activity, following a high-profile attack on the Washington police department.
It is believed that the hackers renamed their “leak site” to Payload.bin, and now the group provides it to other criminals as a third-party hosting, where you can lease someone’s files without starting your own site for this purpose.
It is not yet clear whether the authors of Babuk Locker tried to sell their builder to a third party (and he got into the network as a result of an unsuccessful deal), or someone from the group’s competitors or cybersecurity experts arranged the leak.
The Babuk constructor was also leaked two weeks after the source code of the Paradise ransomware constructor was also posted on a public hacker forum.
While the two incidents are believed to be unrelated, both are of concern to cybersecurity experts who believe that cybercriminal gangs will now use the two tools for future and potentially devastating attacks.
Let me remind you that I also wrote that Clop ransomware continues to work even after a series of arrests.