The first hacking attacks and the realization of the danger of trusting information to the digital media became a shock to computer users. That’s when the question of data protection rose, and the development of the first antivirus programs began. And that was even before the Internet became a usual thing. Nowadays, when every home is a part of the network, it is vital to protect data. Here, we shall list and speculate on the most effective yet doable data security measures.
What Is Data Protection?
People have been practicing data protection since ancient times. Imagine a messenger running from one city to another, carrying a ribbon with seemingly random letters. Or a medieval scribe who makes copies of his manuscripts. Both were protecting data. The runner was using a scytale encoding to keep the message from being read by enemies should he even be caught. The writer made a copy of the text to hide it in a chest to protect it from wind, rain, snow, and thieves. Today we do the same things, but the threats are different.
Data protection encompasses any measures we take to secure data regardless of where it is stored: on a remote server or a hard disk of our computer. These measures include inputting passwords to any devices or Internet accounts, undergoing biometric authentication, installing antivirus software, conducting regular scans, etc. These measures can be arbitrary or obligatory.
What Are Data Protection Regulations?
People’s attitude to the security of their private data can be astoundingly careless. But it’s their problem. On the contrary, those companies who take responsibility for storing or processing their clients’ personal data (like social networks or electronic mailboxes, state registries, public services, etc.) oblige themselves or are obliged by law to implement data protection regulations within their workspace. An example of such obligatory guidelines is GDPR, the International General Data Protection Regulations accepted in the European Union in 2018.
Why Is it Important?
One can hardly find a modern industry that would not rely on information technologies or involve them. Criminals and thieves of all sorts now have a new catch – information. Computer hackers can steal information, destroy it, blackmail owners with its disclosure, or encrypt the data on hacked computers. Then they can demand a ransom from their victims for having their data decrypted. The last case is the first viable and widely-used hacker business scheme – a ransomware attack. In a world where all person’s work, private life, plans, notes, and even dreams become the content of a portable device – the security of this content becomes crucial, and its loss can be deplorable.
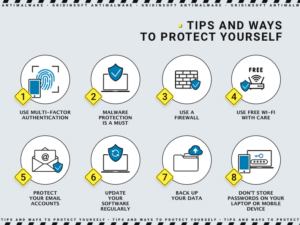
Tips & Ways to Protect Yourself
What is very important to remember is that although various internet services comply with their data security policies and regulations, users should cooperate with these services and not overthrow all the responsibility for the safety of their data on the corporations. The following list of data-safety measures is good for protecting data on a personal device and the cloud.
1. Set up two-factor authentication on your financial accounts. Financial accounts are usually more protected than social media profiles, mailboxes, or messengers, but they require more attention and care. A breach of a bank account is like nothing you want to experience. Therefore, use the two-factor authentication in your banking service to protect yourself from fraud, deceptive social engineering, and phishing attacks. All it takes is to press a button on your telephone every time you try to access your banking account. If any crooks get your login and password, you won’t let them use those credentials.
2. Malware protection is a must. Without an anti-malware solution any system today is bare against a jungle of harmful entities. A modern security program will 1) warn you about suspicious webpages you are trying to access, 2) stop you from entering overtly dangerous sites, 3) quarantine and remove any recognizable malicious programs as soon as they end up on your device, 4) clear all hidden threats with the help of a deep scan function.
GridinSoft Anti-Malware is a versatile solution featuring all the described functions and providing consistent protection without inconveniences typical for bulky and “heavy” antivirus programs. Economically beneficial, Anti-Malware is one of the most efficient and quick security programs on the market.
3. Use a firewall. A firewall is a program filter separating a network it protects from the external environment. It can be protecting one computer or an entire workgroup. Most of the OSs have an in-built firewall. It controls the incoming and outbound traffic using pre-defined rules. Users tend to switch off firewalls temporarily to access suspicious websites but later forget to reactivate the defense. That is dangerous and puts a device or a network at risk.
4. Use free Wi-Fi with care. A Wi-Fi router can be a source of a so-called Man-in-the-middle attack that uses a spoofed network name. After you access the wrong network by mistake, all the data outbound from your device comes into the possession of crooks. Later your data can be used directly against you up to identity theft or blackmailing, or, in better cases, it can be collected and sold to third parties for their own needs.
5. Protect your email accounts. An email account is the core of any person’s virtual representation. Profiles in social media and other internet services often refer to your email address, and that address is essential to password restoration if you happen to need that. Therefore, email safety should be of the utmost concern. Remember to log out from your mailbox on any device except for yours. Also, make sure you use a strong password and change passwords from time to time.
6. Update your software regularly. Computer software nowadays gets updated automatically or with the slightest effort from the user. However, many program vulnerabilities emerge in in-between moments, when one program (let’s say operating system) is already updated, while some different software is not yet up-to-date. Such inconsistent versions can lead to malware infection if cybercriminals intend to pull that over. The most wanted updates are the updates of security programs. The more malware signatures an antivirus program has in its libraries, the more malicious items it will remove from your PC before they can even harm it.
7. Back up your data. Advice to have a backup of all critical information to preempt physical damage of the drive, loss, or theft is one of the wisest hints one could harken to. Anyone who has ever experienced anything mentioned above knows how important it is to have everything in two or maybe even three instances.
8. Don’t store passwords on your laptop or mobile device. Always consider that your portable device might get into someone else’s hands. It might be a good person, but some bad person might also steal your device. You must be ready for such an unfortunate event. And that means not only photos and videos you wouldn’t like anyone to see should not be there on your device, but definitely, passwords should not be stored thereon. By the way, don’t forget to log out from all the accounts remotely when you notice your device is gone.
Always know what you are doing on the web. This tip is not as silly as it sounds. Advertising banners that lead users from one site to another create a wave of curiosity. At first, the user thinks that he or she is surfing that wave, but eventually, it turns out that this wave pushes the user towards dangerous websites that can be filled with scripts – commands that the operating system will start executing if no security software stops this process. These scripts can be the beginning of an automatized malware attack.



1 comment