Palo Alto Networks has discovered the PgMiner botnet, which attacks and breaks into poorly protected PostgreSQL DBs in order to install miners.
A new Linux-based cryptocurrency mining botnet exploits PostgreSQL’s Remote Code Execution (RCE) vulnerability, which compromises cryptojacking database servers.
Cryptojacking (or simply malicious coin mining) is a common way for malware authors to monetize their operations.
Palo Alto Networks has named the new cryptocurrency mining botnet “PGMiner” after its delivery channel and mining mode.
The PgMiner botnet operates according to a well-known and well-established by criminals scheme: it randomly selects a range of IP addresses (for example, 18.xxx.xxx.xxx) and then enumerates all parts of this range looking for systems with an open port 5432 (PostgreSQL).
PostgreSQL is one of the most commonly used open-source relational database management systems (DBMS) for production environments. According to DB-Engines, PostgreSQL is ranked fourth among all database management systems (DBMS) as of November 2020.
If the botnet detects an active PostgreSQL system, it moves from the scanning phase to a brute-force attack, during which it tries a long list of passwords in an attempt to guess the login and password of the default PostgreSQL account (postgres).
If the database owner forgot to disable this account or did not change the password, hackers gain access to the database and then use the COPY from PROGRAM function (CVE-2019-9193 was associated with it, though many in the PostgreSQL community refused to recognize as a bug) to expand access and reach the server and its OS. Having established control over the infected system, the PgMiner operators deploy a miner on the infected server for mining the Monero cryptocurrency.
According to the researchers, the botnet is currently able to install miners only on Linux MIPS, ARM and x64 platforms.
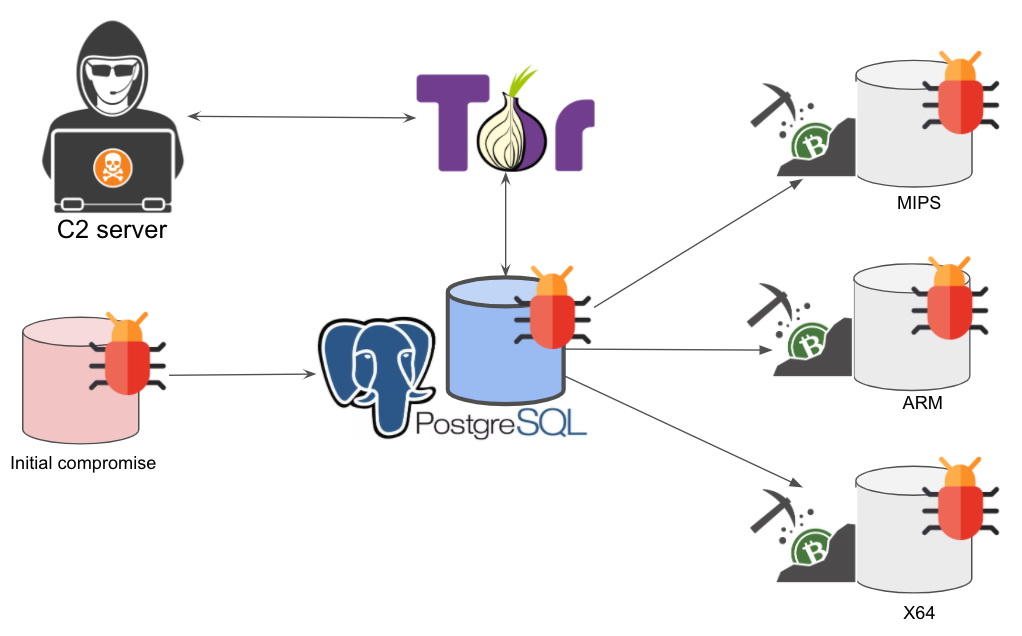
Experts also mention that the PgMiner control server, from which hackers control infected bots, is hosted in Tor, and the botnet’s codebase resembles another similar malware – SystemdMiner.
Let me remind you that hackers cracked European supercomputers and forced them to mine cryptocurrency.

