News, Tips, Security Lab
MITRE NERVE Hacked, Service Taken Offline
MITRE reports about hacker activity in their NERVE network, spotted in April 2024. Upon detecting the suspicious activity, the organization…
RegAsm.exe
The RegAsm.exe process is an important component of the Windows operating system associated with the .NET Framework. This utility is…
LabHost Phishing Service Taken Down by Police
Authorities have seized the LabHost phishing service, accused of stealing personal information from victims worldwide. This service specialized in creating…
Virus:Win32/Expiro
Virus:Win32/Expiro is a detection of Microsoft Defender that refers to a malware with backdoor capabilities. It allows attackers to control…
Cisco Talos Warns of a Massive Brute Force Wave
The Cisco Talos security team has released information about a new campaign of attackers targeting mass account compromise. Specialists have…
Script-Based Malware
Over the last four years, the share of script-based attacks of malware offenses worldwide has grown so drastically that it raised alerts among security specialists and ordinary users. In this…
Critical PAN-OS Command Injection Flaw Exploited
Palo Alto Networks warns its customers regarding a vulnerability in their PAN-OS, that leads to command injection. Residing in their GlobalProtect feature, and requiring some specific configurations, this flaw still…
Fake Robux Generators Spread on Government Websites
Huge number of fake Robux generators recently appeared on a range of websites with .gov, .mil, and edu. They commonly pose as PDF files, enriched with keywords that boost their…
Critical LG TV Vulnerabilities Allow for Command Execution
LG reports fixing four critical vulnerabilities discovered in many of its TVs. These vulnerabilities were found back in 2023, and could allow malicious actors to gain control of affected LG…
List of Scammer Phone Numbers 2024
Telephones have long been integral to everyday life, and scammers couldn’t help but take advantage of them. Although making random calls is as old as the world, sometimes the calls…
Stopabit Virus
Stopabit is an unwanted application that can steal sensitive data. One of its primary functions involves browser hijacking, enabling it to intercept and collect sensitive input data, focusing on capturing…
“Account restrictions are preventing this user from signing in”
When working with Windows, users may sometimes encounter the “Account restrictions are preventing this user from signing in” error. This problem can cause significant inconvenience, up to complete inability to…
SMApps Virus
SMApps is a malicious program that aims at spreading illegal promotions. It mainly attacks browsers by changing settings and redirecting search queries from Google to suspicious sites. Possible distribution methods…
Hunt Ransomware ([email protected])
Hunt ransomware is a new sample of the Dharma/CrySis ransomware family that appeared on April 5, 2024. This malware aims at encrypting the files and asking a ransom payment for…
Two Android Zero-Day Flaws in Google Pixel Exploited
Google has disclosed that two Android zero-day security vulnerabilities have been detected in its Pixel smartphones. The patch is already available, as Google claimed fixing the flaws in the recent…
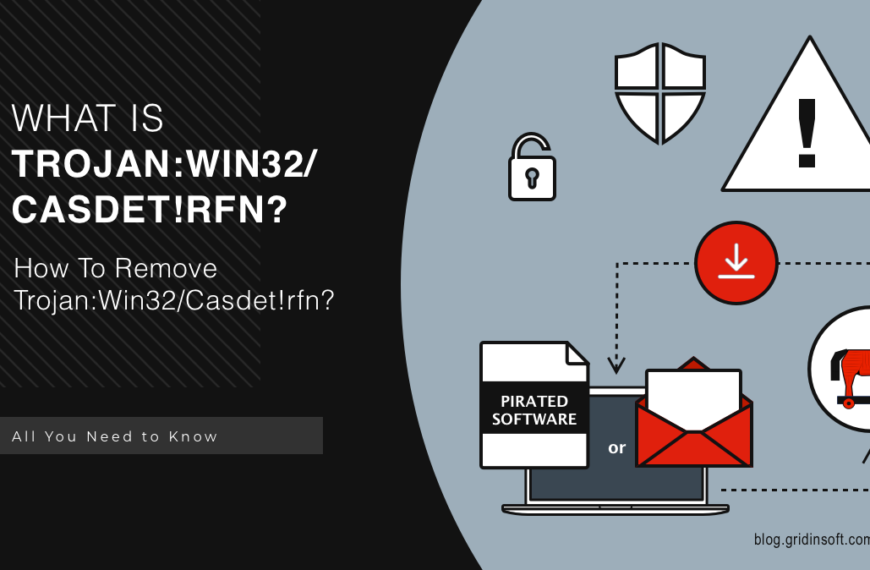
Trojan:Win32/Casdet!rfn
Trojan:Win32/Casdet!rfn is a detection that indicates the possible presence of malware on your system. Users may encounter this detection after using pirated software or opening suspicious email attachments. In certain…
Progress Flowmon Command Injection Flaw Discovered
Progress Flowmon, a popular network monitoring software solution, appears to be vulnerable to arbitrary command injection. Successful exploitation of the flaw can grant adversaries with full access to the network…