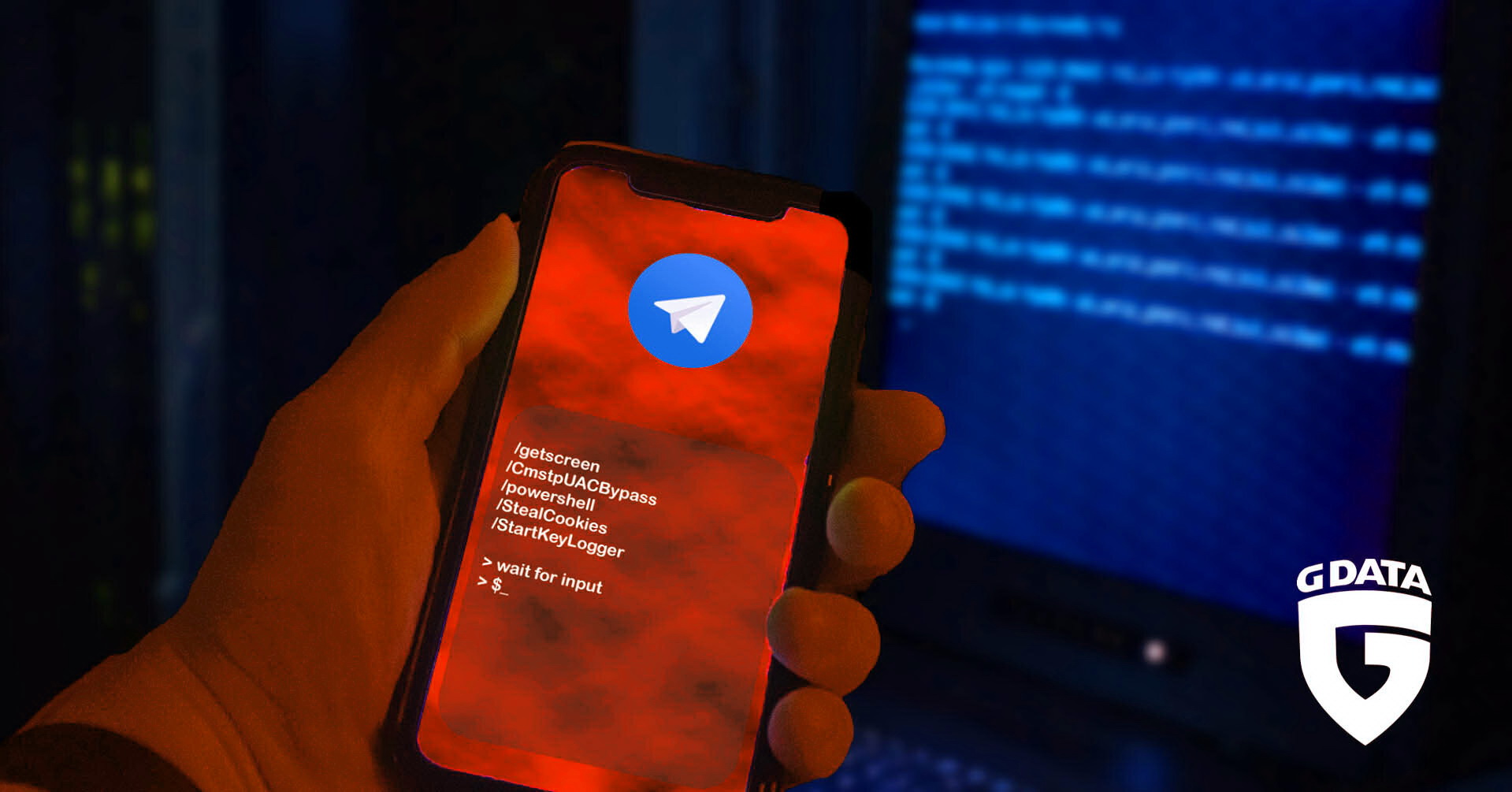
G DATA’s specialists have published a report on the new T-RAT malware, which is being distributed for only $45. The main feature of the malware is that T-RAT allows controlling infected systems through the Telegram channel, and not through the web administration panel, as it is usually done.
Malware creators claim that this provides faster and easier access to infected computers from anywhere, and allows them to quickly steal data. However, T-RAT can also be controlled by more traditional methods, for example via RDP and VNC.
In addition, T-RAT owners can use a special mechanism for capturing data from the clipboard, which replaces strings similar to addresses of cryptocurrency and electronic wallets with the addresses of attackers. This allows successfully intercepting Qiwi, WMR, WMZ, WME, WMX, Yandex.Money, Payeer, CC, BTC, BTCG, Ripple, Dogecoin and Tron transactions.
The malware is also capable of working with terminal commands (CMD and PowerShell), blocking the victim’s access to certain sites (for example, antivirus and technical support sites), eliminating specific processes (disabling security and debugging software), and even deactivating the Taskbar and Task Manager.
G DATA experts write that T-RAT is just one of many families of malware that are equipped with the ability to control via Telegram, and this is not the first RAT that operates on such a model. So, similar functionality is possessed by: RATAttack (targeting Windows), HeroRAT (targeting Android), TeleRAT (used mainly against users from Iran, targeting Android), IRRAT (targeting Android), RAT-via-Telegram (available at GitHub, targeting Windows users) and Telegram-RAT (available on GitHub, targeting Windows users).
Let me remind fans of classic horror stories about viruses and monsters that Alien malware that steals passwords from 226 Android apps.