Viruses are very tricky and even after the scan with reliable anti-malware you still can feel inconveniences while using computer or you don’t know how to interpret the result of the scan or the expected result is not received (full scan indicates that no threats have been found while you are sure there is a problem on the computer). In this case, our Support Center can help you.
In order to provide you with the most complete and qualified help, we need detailed information about your computer, the programs that are installed and the previous scan results.
We have compiled a set of Tools that will help you easily collect the information you need to get qualified help as quickly as possible:
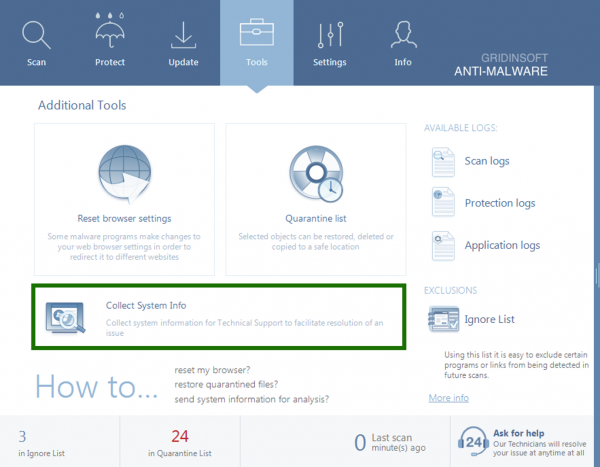
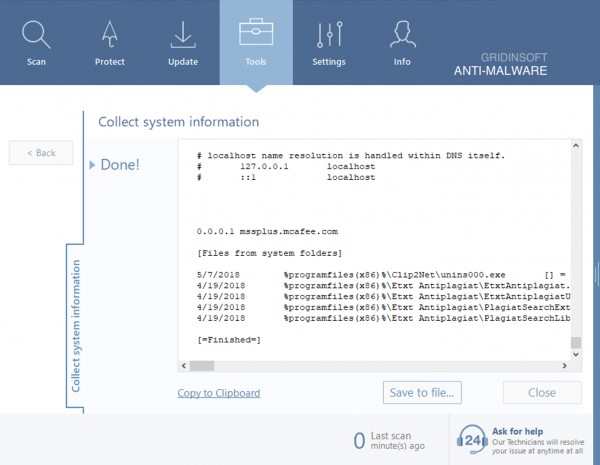
Collect system information. Gathers all needed information about the state of your PC. We need it to analyze the actual vulnerability status of your computer. It helps to understand why some threats weren’t found or weren’t deleted, because some of them can appear on your computer not as separate files, but as running tasks and processes.
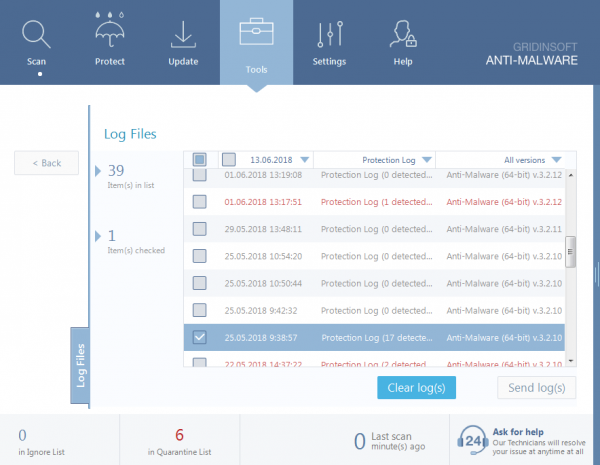
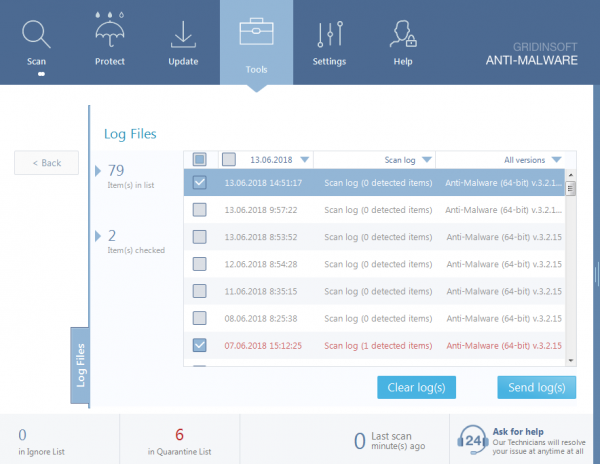
Log files. There are three types in the program, each collects information about specific parts of work:
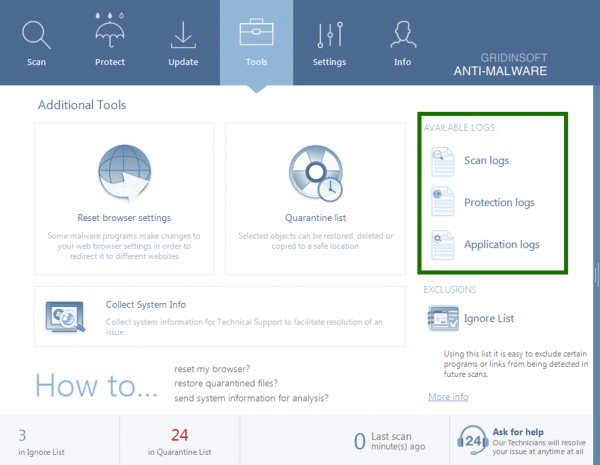
- Application Log. Gathers data about actions of the program, fixates information about possible problems when the program performs starting, scanning or other tasks.
- Protection Log is a detailed log about results of work of three real-time protection systems. If you have any suspicion of conflict in the work with other programs, while Internet Security and On-Run Protection are turned on, we see it in Protection Log.
- Scan Log contains a detailed report of scan results: the scan time, its type, which objects were scanned, and what threats were detected.
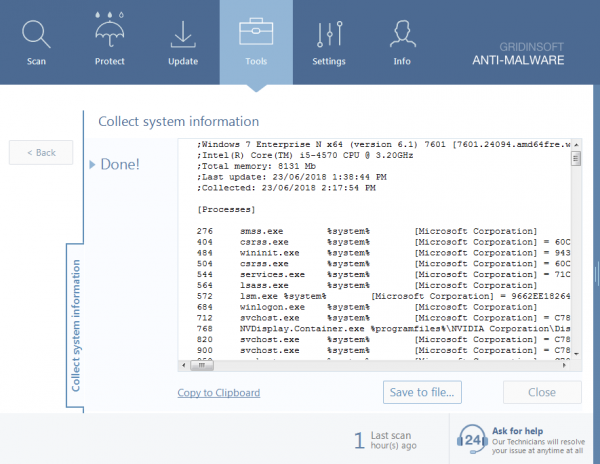
To send us system information for analysis, go to the Tools tab, and select Collect system information. After this information will be generated. Save it on your computer by selecting Save … and send it to us for detailed analysis.
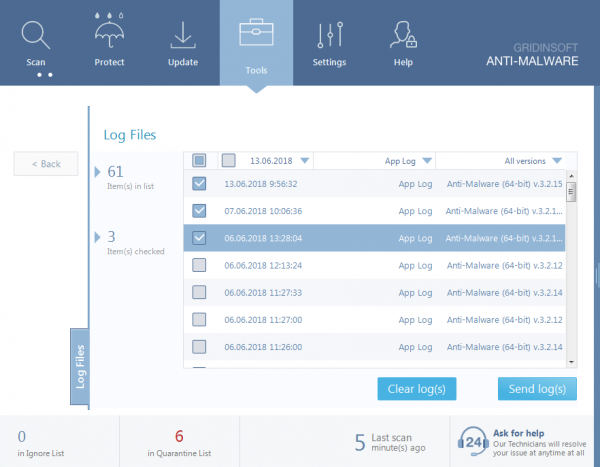
To send us a log file – go to the Tools tab and select the desired report type (Scan Log, Protection Log or Application Log) – check the specific log(s) and send it to us for analysis.
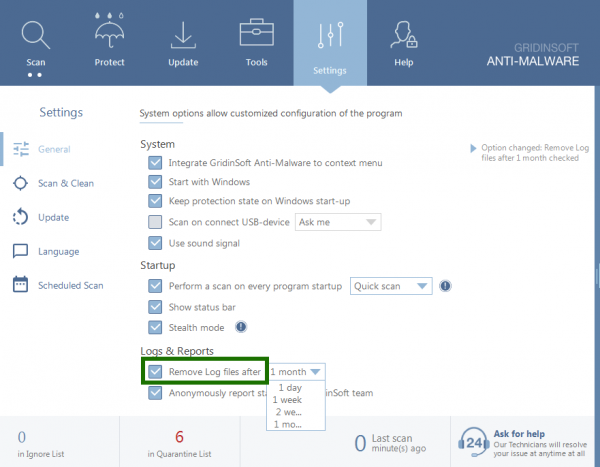
Also in the program settings, you can choose after how many days software stores log files. If this menu item is not checked, the log files won’t be deleted from your computer, which will very helpful in finding the cause of the problem, if it occurs.


how to remove .reha virus from laptop
Envío la recopilación de información del sistema para saber si se puede solucionar y restaurar los archivos infectados con .npsk
Por favor como restaurar los archivos .npsk
comment supprimer le virus ooxa s;il vous plait
How to restored rzfu files