Android malware is a common name for all malicious software present in Android. This OS appears not only on phones but also on a vast majority of IoT devices. Things like smart fridges, irons, coffee machines, and microwave ovens run Android as well and are vulnerable to the same malicious programs. What is Android malware, how to detect it and clean your device – let’s figure that out.
What is Android malware?
Generally speaking, malware term explains a lot about the functionality of such software. Those are programs that aim at malicious activity inside of the attacked device. It may range from stealing personal information and spying on the user to spamming advertisements all over the screen. The main difference from malware for computers that appears at a glance is the fact this malware is created and compiled for Android. As a UNIX-like OS, it features system calls and security measures that differ from the ones in Windows. But that still does not create a lot of difference.
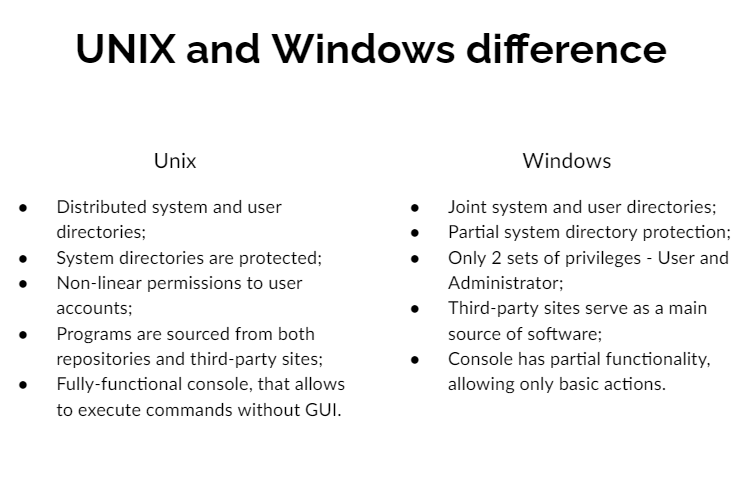
The biggest contrast between Windows and Android malware is its spreading form. So-called Trojan viruses are present in both cases, but the use of such a spreading form is not equal. While most malware for Windows comes as a tiny app that hides somewhere in the system, Android malware generally opts for a trojan form. Malignant stuff is available directly at the Google Play Store – a general place to get apps for Android phones. A tiny share of malicious software is spread on forums, as third-party apps that are installed manually. Those things are usually the most dangerous ones.
How dangerous is Android malware?
Same as any other malware. Properties of malicious software types remain the same, regardless of the platform they are launched on. Adware will flood your phone or tablet with numerous banners that will pop up at the most inconvenient moment. Rogue apps will spam you with numerous alerts regarding non-existing issues. Backdoors will grant control of your device to a third party. Stealers and spyware grab any possible kind of information about you and your device.
The two latter categories are worth a separate description since they’re one of the most widespread. Mobile devices, which expose 65% of all Android devices, contain a huge amount of personal information. Actually, while PCs may hold confidential information related to your job or other activity, smartphones keep your very personal information. Hence, targeting spyware upon smartphones is way more resultative and profitable.
Android malware forms
As I have mentioned above, the most common form of Android malware is a trojan. That supposes the use of a disguise of a legit app to deceive the users and force them to install it. Google Play Store has a pretty poor moderation, and cybercriminals exploit it with pleasure. Some malware may remain listed months after being detected and reported to the Google team. And they are hard to distinguish from regular programs – threat actors never disdain to use review spoofing.
Another feature that is proper for Android and makes it easier to create malicious applications is Android Studio. It is a free user-friendly IDE that offers zero-code functionality for app creation. Such a thing is convenient when you want to create something exclusively for your purposes, and don’t want to spend a lot of time studying Java. Simultaneously, it grants the scoundrels the ability to quickly create a disguise for their malignant thing. Nonetheless, the most famous and dangerous Android malware examples usually feature well-designed interfaces, rather than a zero-code craft from Android Studio.
Most often disguises
Family trackers, alternative clients for different messengers, navigation apps, and basic utilities – we used to trust such apps. At the same time, they naturally require access to the functions which are useful for malicious use. Tracking the device location, and access to your chats and social media accounts – are you sure that app developers use them properly? Certainly, being paranoid about your privacy is no good as well, but every user should consider the risk of using no-name apps.
In certain cases, malicious programs can ask for rights that differ from their declared functionality. Engineering calculators can barely make use of your gallery. Photo editing software should not have the ability to make calls and access your gallery. However, such misuses are rare – most of the time, hackers try to mask their access to your confidential information under the guise of a legit request.
Here are the most common app types that crooks use as a disguise:
- GPS tracking software;
- Navigation apps;
- SMS spam filters;
- Alternative clients for Messenger, WhatsApp, Telegram, Twitter, etc.;
- Alternative contact books;
- Photo editing apps;
- Utilities for gaining root access.
How is Android malware promoted?
Creating the app and uploading it to Google Play Store is only a part of the malware spreading process. To make the victims download the virus, crooks should promote it. The most common ways to spread it across the folks are banners in different apps and offers on forums. Other methods include browser redirects with an offer to install “a very popular app”. They may call for different motivations and apply various tricks, but the sole purpose is to force the user to press the “Install” button in the Play Store.
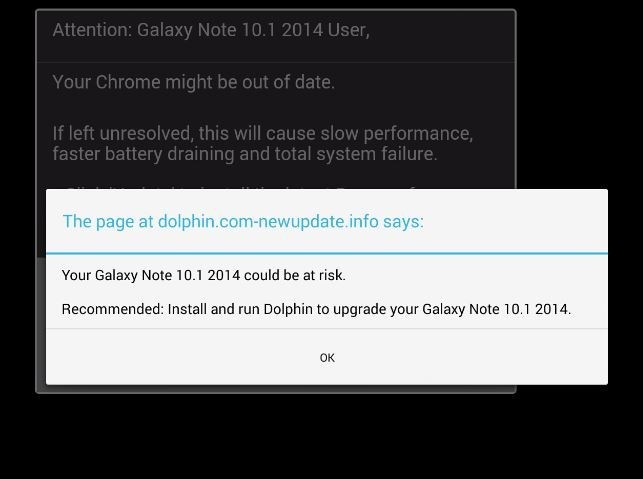
Malware that uses a more concealed form and does not have a visible app usually gets on users’ devices through third-party sources. Contrary to iOS, Android allows users to install application packages from wherever they get them. And that is a severe security flaw, as you voluntarily download and install malware to your phone.
Some really rare viruses rely upon vulnerability exploitation. In those cases, users are pretty much helpless against these things. Cybersecurity researchers witnessed cases when it was enough to send a message in a social network, and a vulnerable app (or a third-party client) was executing malicious code on its own. Most common cases, however, do not use zero-click exploits and prefer more available breaches. Social engineering remains a very effective way to make the victim act as hackers want to.
Most notorious examples of malware for Android
Among hundreds and thousands of malware examples, only a few of the best malware can be called worth mentioning. Let’s have a look at those favourites – at least the ones that gained fame.
Flubot Stealer
Flubot is an example of stealer malware, that is famous for its spreading way. To deliver it, hackers were using SMS phishing which mimicked the package delivery notification. These SMS contained a malware downloading link and a text or a voice message, that instructed the victims to follow the link. After the successful installation, Flubot accesses the phone book and starts sending the same messages to other victims. That made its spreading exponential. Such a behaviour is similar to what network worms do – with the only difference being that the latter usually use email messages to self-spread.
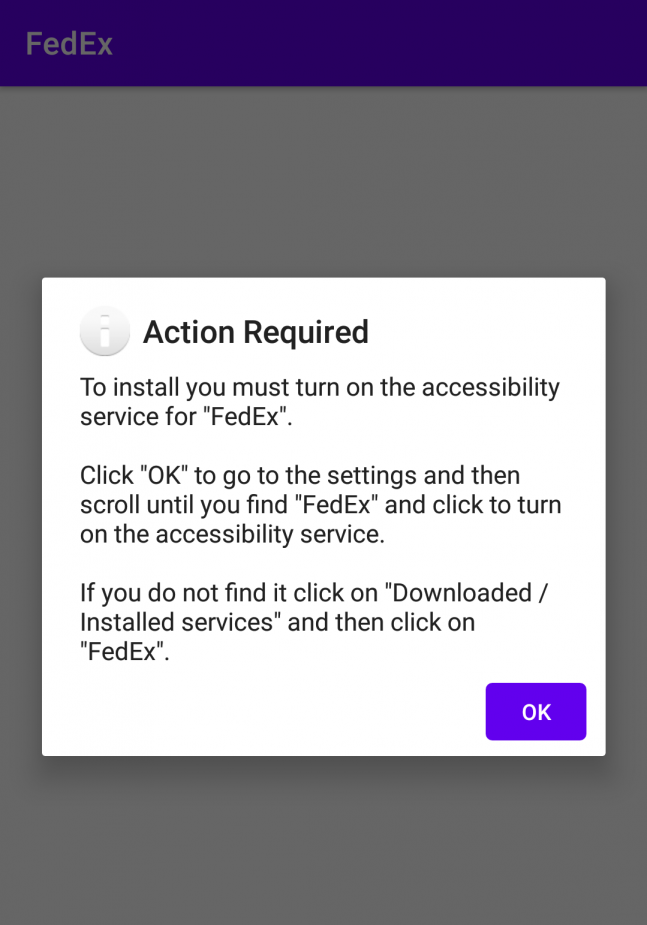
Typical targets within the attacked system are banking and cryptocurrency credentials. As you can imagine, being infected with the Flubot may end up with huge money losses. Despite the fact that Europol managed to capture the key group of distributors, it still appears here and there.
Joker
Joker is a pretty old malware that appeared back in 2017. It got different classifications – from spyware to adware and fleeceware (the sub-specimen of unwanted programs). The key danger it carries is hidden subscriptions its victim agrees voluntarily. In fact, Joker shows dozens of popups that offer the user to claim a reward for the quizzes it never took part in. Clicking through the sites malware throws on the victim, it agrees to subscribe to different paid services online. Further, these services will flood the user’s device with various other scum. For sure, Joker makes its victims suffer for their own money.
This malware spreads through spoofed apps in the Play Store. Crooks may apply to create a stand-alone disguise, as well as mimic some well-known applications, copying their name and description. A lot of apps with Joker inside received over 100,000 installations – so you can imagine its spreadness.
xHelper Downloader
First seen in March 2019, xHelper recommended itself as a tough nut. Contrary to different other malware examples, it featured anti-detection and anti-removal capabilities that made it hard to deal with. It was integrating so deeply into the system that even factory resets were useless for its removal. By the end of the year of 2019, it became enormously widespread and was listed as the most prevalent malware. For the first 6 months of its activity, xHelper scored over 45,000 victims.
The key functionality of this malware is delivering other malware to the attacked device. Generally, it was different spyware samples – access to the network of infected devices was available for sale on the Darknet. Some versions also featured a less concealed approach, spamming the victims with numerous advertisements. Malware analysts ensure that these were the functions of xHelper, not the malware it delivered.
It has seen distribution in different forms, both Trojan apps in the Play Store and as a separate file. One of the most popular disguises back in 2019 was a New2048HD game. Rascals likely try to catch all possible trends, so it is obvious to expect it under different other disguises.
Pegasus Spyware
One of the most infamous malware, developed by NSO Group, the subsidiary of the Israeli government. This program was originally designed as a tool for government-grade spying – an important task for special services like the FBI or Mossad. It fits both Android and iOS. NSO offers its brainchild to governments of different countries. These days, over 40 countries around the globe use this tool for obvious purposes. The developer signs a contract with each country, where they agree on all aspects of the malware application. There is also a brother-in-law – Chrysaor malware – pretty much the same thing but with minor adjustments to be more effective on the newest Android versions.
By the functionality, it is a classic example of professionally-made spyware. It can track locations, extract all kinds of files, read chats and SMS messages, access galleries and record calls. To have real-time information about the victim, Pegasus can enable microphones and cameras. Overall, getting this thing on your device means all the private information is not private anymore.
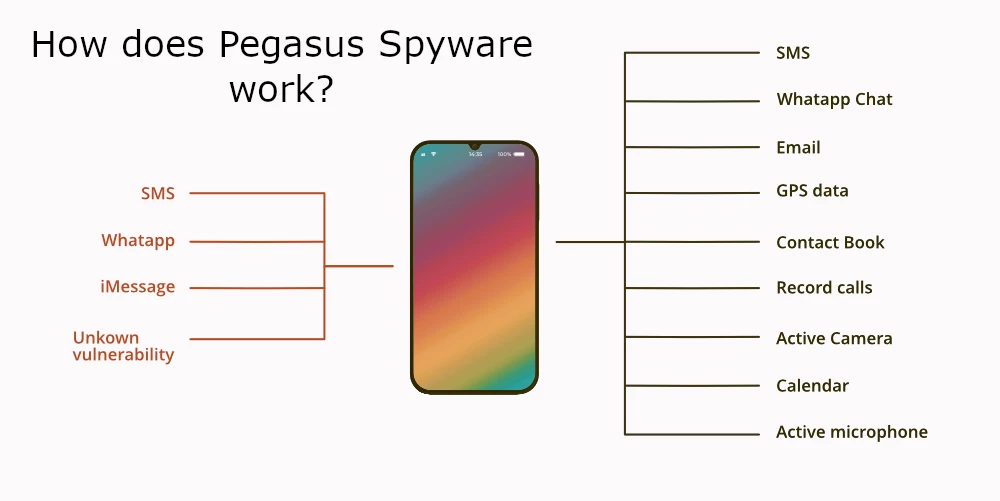
Ways of spreading the Pegasus users opt for are as sophisticated as the exact malware. The key bearing point is various exploits present in operating systems and application software. Main penetration points were vulnerable link handling mechanisms in default messaging apps, and breaches in WhatsApp. These security violations made it possible to inject Pegasus Spyware without any interaction from the user.
Teabot RAT
Teabot is the youngest malware example in that list. Its first appearance happened at the dawn of 2021. Nonetheless, its peak activity started a year later – in February 2022. Remote-access trojan offers the ability to record the victim’s screen and steal credentials, mainly ones related to banking, insurance accounts, and cryptocurrency wallets. It features some anti-detection measures – mainly, code string obfuscation.
Spreading ways of Teabot RAT are somewhat similar to Joker malware, with one difference. Instead of downloading the program which contains Teabot, victims get dropper malware. It tricks the user to allow the app to install the .apk files from third-party sources. Then, it asks for an “update”, which actually contains the payload. Early samples, however, were primarily spread through smishing, i.e. without the precursive dropper stage.
Eventbot Banker
Eventbot is a pretty unusual malware, because of the way it violates privacy and gets to the users’ data. Analysts spotted it first around March 2020, and it keeps running today. This banking trojan works as a keylogger but makes this in its unique way. In order to extend its abilities within the system, Eventbot tricks the user to permit him to use accessibility features. The latter allows the trojan to open banking apps. Then, it intercepts the login credentials by pasting them into the form via gestures and similar accessibility actions. With such an approach, malware can attack over 180 mobile banking apps from all over the world. The list includes Barclays, Revolut, HSBC UK, Coinbase, and Paypal.
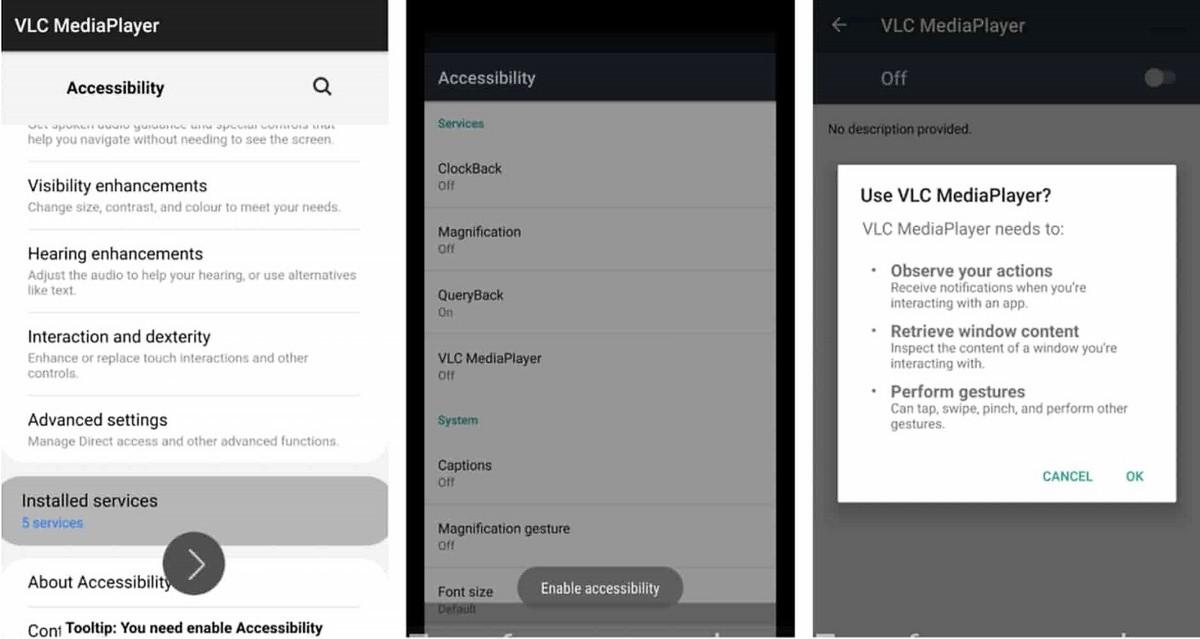
The way it gets into the targeted device is also interesting. First, it appears as an ordinary app, installed by an urgent request from a certain website. As you can suppose, this request is completely fake. Then, this pseudo-updater asks permission to use accessibility features and then requests to run in the background. After that, Eventbot deletes itself from the launcher, hence there’s no way to find and remove it manually.
How to avoid viruses on Android?
As you can see from the paragraphs above, most malicious programs for Android rely on users’ inattention. Actually, malware for computers does the same – but there are many more examples of whether it tries to slip in through exploits. Androids are different in their internal structure and overall actions the users typically do. That’s why social engineering and exploiting low awareness are prevalent when it comes to Android malware. Hence, it is quite easy to find ways to prevent this mess.
Never follow browser redirects. You can face the situation when clicking the link opens not just a page in your current browser tab, but also an additional tab with different content. In some cases, pressing the link may throw you to a completely different page – not even close to what you expect to see. Benevolent and well-known sites will never do that – unless they’re compromised, of course. The redirect pages commonly contain dubious offers, like installing certain apps or enabling pop-ups. No way it will bring something useful for you.
Be sceptical about the links in messages. Never trust messages from strangers which have links. Even if your friend texts you, but the message looks strange and non-typical – consider checking it before following. You can never be sure if that friend was not hacked. Even worse idea is opening those links and following the instructions it shows you.
Use only trusted software. The Play Store contains an enormous amount of applications – 2,78 million. Considering all of them dangerous is wrong, but the vast majority of them will not be useful either. When you need decent software that will not violate your privacy and act as a downloader for malware, check the forums and see what folks advise. There could also be threads on different forums regarding certain app, where you can get exhaustive information about the program.
Use anti-malware software. Both sophisticated and clumsy-made Android malware can be successfully stopped at early stages. All you need to have is a proper anti-malware solution that will thoroughly scan your device time-to-time. Although the value of antivirus software for Android may be underestimated, it is a really useful addition to your phone security. Consider trying out GridinSoft Trojan Scanner – free antivirus for Android. It will effectively scan your device with different scanning systems, without any impact on your device’s performance.


I bought a TCL cell phone with the unnecessary Facebook app factory-installed after disabling was a trojan verse app, with several hidden Facebook malware apps spreading malware thought out 5 other devices. No one is putting the blame on Facebook when all of the app’s lead to Facebook login.
Facebook is a scam wake up people.